Case #
When logging into your Azure App Service you encounter the following error: "An error occurred while sending the request. Unable to read data from the transport connection: An existing connection was forcibly closed by the remote host."
The above error can manifest with different error messages:
- The request was aborted: Could not create SSL/TLS secure channel.
OR
- Could Not Establish Trust Relationship for the SSL/TLS Secure Channel with Authority [authority name, i.e. domain name included in the TLS certificate].
You have checked that there is no issue between the Azure App Service connection to your SQL datastore (Azure SQL, Azure database for MySQL, etc). You have also checked your App Service code with remote debugging and have checked all application and server logs.
Solution #
You need to check the following possible root causes:
- Certificate signatures are valid.
- The certificates have not expired
- The certificates are not self-signed.
- Certificate chain ends at a trusted root.
- All TLS intermediate end root certificates are in the clients' trusted root certification authority certificate store.
- Certificate chain has valid basic constraints
- The TLS certificate has a successful revocation check and the TLS certificate has not been revoked. Ensure that the CRL endpoint is accessible.
To resolve error "An existing connection was forcibly closed by the remote host" you need to test all available versions of TLS which are accepted at a minimum by your App Service. In some cases, you may need to set this setting to minimum TLS version 1.0 or TLS 1.1, as shown in the below diagram. From the Azure management portal, you should navigate to your App Service --> Settings --> TLS/SSL settings.
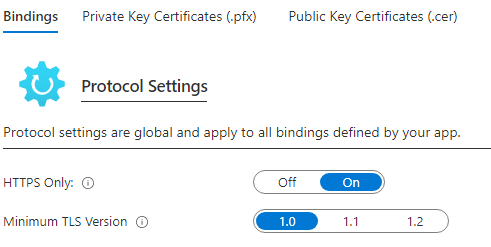
Bear in mind that if this is the case with your App Service, you will eventually need to update your code to support at least TLS 1.2 protocol version. TLS 1.3 is coming out soon and there are serious reasons why App Services should reject TLS 1.0 and TLS 1.1. There are security and compatibility reasons. The compatibility reasons relate to Azure App service support for these old TLS versions. The security reasons behind deprecation of TLS 1.0/1.1 are detailed in the followign article: https://www.digicert.com/blog/depreciating-tls-1-0-and-1-1.
For a more detailed description about the deprecation status of TLS 1.0/1.1 in Azure services, you can review the following article of this blog: https://stefanos.cloud/tls-1-0-and-1-1-deprecation-in-azure-services/.



