Overview
Some of TLS protocols (TLS 1.0 and TLS 1.1) as well as ciphers suites (3DES - TLS_RSA_WITH_3DES_EDE_CBC_SHA) are gradually being deprecated from all software systems (client and server). This undoubtably affects Azure services as well. If there is a mismatch in the TLS configuration among the components of your Azure solution, you may encounter authentication errors. This article discusses the TLS 1.0 and 1.1 deprecation in Azure services. You should also review the following article with all discontinued services in Microsoft Azure.
Azure AD deprecation of TLS 1.0 and TLS 1.1
On January 31, 2022, Microsoft has announced that it will stop supporting TLS 1.0 and TLS 1.1 in Azure AD.
Applications which are communicating with or authenticating against Azure Active Directory might not work as expected if they are NOT able to use TLS 1.2 to communicate. This situation includes Azure AD Connect, Azure AD PowerShell, Azure AD Application Proxy connectors, PTA agents, legacy browsers, and applications that are integrated with Azure AD. To maintain a secure connection to Azure Active Directory (Azure AD) and Microsoft 365 services, Microsoft has complied a list of action items to ensure that your client apps and client and server operating system (OS) are enabled for TLS 1.2 and modern cipher suites.
TLS protocol supportability for other Azure Resource Providers
The following article provides the end of support dates for various Azure Resource Providers as well as Microsoft 365, Microsoft Graph and Azure AD Graph services.
The above article also provides a useful Powershell script which can be used to fetch all TLS versions supported by each Azure service.
For example, the following article provides a list of supported security cipher suites currently supported by Azure Front Door: https://docs.microsoft.com/en-us/azure/frontdoor/front-door-faq#what-are-the-current-cipher-suites-supported-by-azure-front-door-&preserve-view=true.
Similar considerations should be made for Azure Storage accounts, as per https://docs.microsoft.com/en-us/azure/storage/common/transport-layer-security-configure-minimum-version?tabs=portal.
Azure Service Bus supports choosing a specific TLS version for namespaces. Currently Azure Service Bus uses TLS 1.2 on public endpoints by default, but TLS 1.0 and TLS 1.1 are still supported for backward compatibility. Azure Service Bus namespaces permit clients to send and receive data with TLS 1.0 and above. To enforce stricter security measures, you can configure your Service Bus namespace to require that clients send and receive data with a newer version of TLS. If a Service Bus namespace requires a minimum version of TLS, then any requests made with an older version will fail. To learn more, see Enforce a minimum required version of Transport Layer Security (TLS) for requests to a Service Bus namespace.
For any other Azure service provider TLS supportability status, you should check for all official Microsoft Azure announcements for TLS 1.2 support and TLS 1.0 and TLS 1.1 deprecation, as per https://azure.microsoft.com/en-us/updates/?query=TLS.
How to update your .NET Azure App Services for TLS 1.2 support
Starting June 30 2018, all new apps in Azure App Service are created with TLS 1.2 by default.
As of this article writing, TLS 1.0/1.1 are still valid options in Azure Public datacenters inside the Azure App Service.
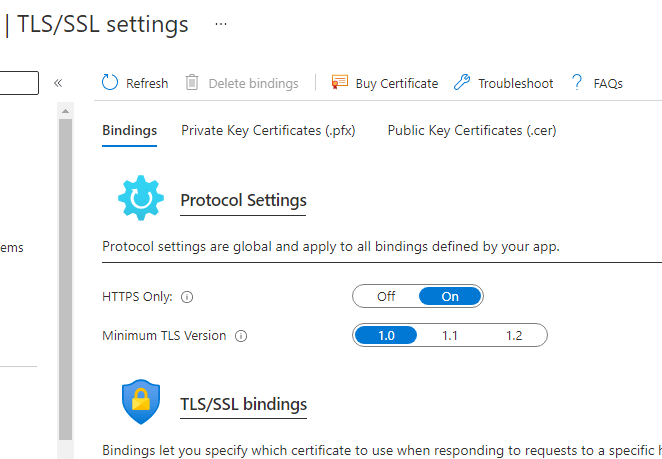
However, given that eventually Azure App Service will deprecate support for TLS 1.0 and TLS 1.1 and in sight of the upcoming TLS 1.3 version (IETF RFV 8446), you should strongly consider updating your Azure App Services as soon as possible for them to become TLS 1.2 compliant.
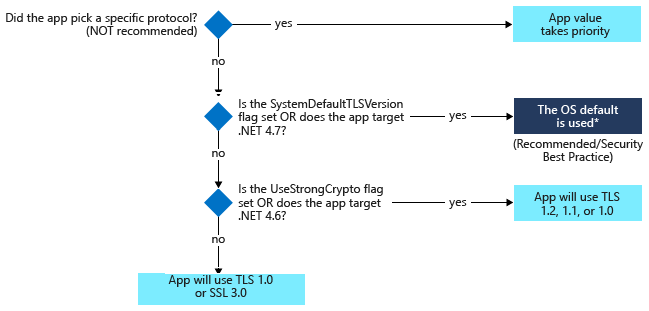
This Microsoft Community article outlines the options for developers to update their Azure App Services to support TLS 1.2 in the case of .NET apps. If you are compiling your code for .NET framework 4.7 (4.7.1 for WCF apps) or later, it will use the default TLS version for the OS. If you complied to a previous .NET framework version, it will use older versions of TLS unless you apply the right patch, and use one of the following methods.
- Set a registry setting to force all .NET code to use strong cryptography
- Set a config setting for the app context overrides to use the strong cryptography
- Add a line of code to change the TLS version used for HTTPS calls
You should also follow Microsoft best practices when re-designing your .NET app code for TLS protocol support, as per https://docs.microsoft.com/en-us/dotnet/framework/network-programming/tls.
Update (15 March 2022):
See the latest Microsoft announcement on TLS 1.0 and 1.1 deprecation dates for Azure Devops services at: https://devblogs.microsoft.com/devops/deprecating-weak-cryptographic-standards-tls-1-0-and-1-1-in-azure-devops-services/.
Some final words on TLS 1.0 problem
There are a lot more considerations to the TLS 1.0 problem than the ones mentioned in this article. These include operating system flaws and updates, Powershell script updates and client/server application code updates. Microsoft has put together a highly informative article about this topic, which is a useful read in your journey towards better security with TLS 1.2+.
Sources
https://docs.microsoft.com/en-us/troubleshoot/azure/active-directory/enable-support-tls-environment