Table of Contents
- Introduction to Citrix Virtual Apps and Desktops design considerations
- Prerequisite knowledge
- The Citrix Consulting Services design methodology
- The Citrix Tech Zone
- General design considerations
- Citrix layered design methodology
- User layer design considerations
- Access layer design considerations
- Resource layer design considerations
- Control layer design considerations
- Hardware layer design considerations
- Horizontal design considerations
- Additional design references
Introduction to Citrix Virtual Apps and Desktops design considerations
Having implemented various on-premises Citrix Virtual Apps and Desktops - VAD (former Citrix XenApp and XenDesktop) infrastructures, i decided to write a, rather long, technical article on Citrix architecture and design best practices. This long guide has it all, from Citrix Virtual Apps and Desktops and Netscaler components to design considerations and best practices. The assumption for the below information is that implementation is to be purely on-premises, unless noted otherwise. There will be references, where needed, to Citrix Cloud design considerations, with one ore more resource locations (on-premises, private cloud or pubic cloud).
Running VDI projects falls under the greater concepts of End User Computing (EUC). EUC is a broad concept that encompasses the technologies and strategies used to enable end-users to remotely access and interact with their computing environments. It revolves around providing a flexible, secure, and efficient remote computing experience to end-users. EUC is a superset which includes all of the following types of virtual computing.
- Virtual Desktop Infrastructure (VDI): VDI is a subset of EUC. It is a technology that allows organizations to host and manage virtual desktops on servers in a centralized data center. End-users remotely access these virtual desktops remotely, typically through thin clients or other devices. VDI provides isolation and customization, making it easier to manage and secure the end-user environment. Citrix Virtual Apps and Desktops (former Citrix XenDesktop) is an example of leading VDI solution. Other on-premise VDI solutions are Microsoft Remote Desktop Services (RDS).
- Server-Based Computing (SBC): SBC is a predecessor to VDI and is also part of the EUC landscape. In SBC, multiple users share a single instance of an application or desktop environment hosted on a server. SBC is known for its efficiency, as it can support a large number of users with relatively low resource requirements. Citrix Virtual Apps (former XenApp) is an example of leading SBC solution. Other on-premise VDI solutions are Microsoft Remote Desktop Services (RDS). Remember that Citrix VAD is strongly dependent on RDS for providing server OS desktops and apps.
- Hosted Shared Desktops: (HSD) Hosted shared desktops are another form of EUC, wherein multiple users share a single virtualized desktop instance. While SBC can refer to both desktops and apps, HSD refers to desktops only which are running on Server OS machines. This approach is efficient in terms of resource utilization but may have limitations in terms of customization and isolation.
- Desktop as a Service (DaaS): DaaS is a cloud-based approach to delivering virtual desktops. It's a subset of VDI and EUC. With DaaS, virtual desktops are hosted and managed in the cloud, reducing the need for on-premises infrastructure. It offers scalability and flexibility, making it a valuable component of EUC.
In the realm of EUC, various types of virtual desktops are available to cater to different use cases and requirements:
- Persistent Virtual Desktops: These virtual desktops are fully customizable for each end-user, allowing them to personalize their desktop environment. Persistent virtual desktops are ideal for users who need consistent and personalized settings.
- Non-Persistent Virtual Desktops: Non-persistent virtual desktops are shared among multiple users and reset to a predefined state after each session. These are suitable for task workers who do not require personalization and for scenarios where a clean, consistent environment is needed.
- Pooled Virtual Desktops: Pooled virtual desktops are a subset of non-persistent desktops. Users can access any available desktop from a pool, and changes are not saved after the session ends. This approach maximizes resource utilization.
- Static virtual desktops. Static virtual desktops are also a subset of non-persistent desktops. The only difference here is that each user always get assigned to the same (static) virtual desktop.
- Remote Application Hosting: While not strictly virtual desktops, this method involves hosting and delivering individual applications to end-users rather than full desktop environments. It's a resource-efficient approach that provides specific applications to users. Microsoft Remote App and Citrix Virtual Apps (former XenApp) are both leading solutions in the remote application hosting area.
Prerequisite knowledge
It is assumed that the reader of this article has fundamental knowledge, and ideally some experience, on the following areas. Some of these areas constitute general IT knowledge, while others are Citrix-specific.
- TCP/IP-based network and storage systems.
- Core Citrix design principles and Citrix Virtual Apps and Desktops architectures.
- Installing and configuring Citrix server roles associated with app and desktop virtualization.
- Backing up components of an app and desktop virtualization environment.
- Troubleshooting environments which include a Citrix app and desktop virtualization solution. You can refer to my Citrix VAD troubleshooting e-book for more details at: https://www.amazon.com/Citrix-Virtual-Apps-Desktops-troubleshooting-ebook/dp/B08LJSYXGR.
- Cloud computing concepts such as private, public, and hybrid clouds.
- Assess environment requirements and learn to apply leading design principles to address them in a multi-site Citrix ADC deployment. Configure different methods of client connection including Citrix Gateway, VPN, Split Tunneling and other proxy configuration options.
The following certifications should be pursued by Citrix architects and engineers interested in proving their knowledge of Citrix architectural and design matters.
- Citrix Certified Expert - Virtualization (CCE-V)
- Citrix Certified Expert - App Delivery and Security (Netscaler)
The Citrix Consulting Services design methodology
Citrix Counsulting Services (CCS) employ the following 5-phase methodology when running VDI projects.
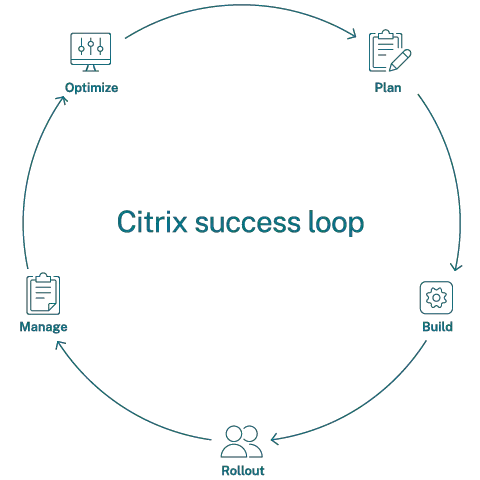
This article mostly covers the "plan" phase of the CCS methodology.
The Citrix Tech Zone
The Citrix Tech Zone is available at https://docs.citrix.com/en-us/tech-zone/about.html and is full of design resources for Citrix architects. All Citrix VAD design decisions are documented at: . The overall design approach is based on the official Citrix design guide available in the Citrix Tech Zone at https://docs.citrix.com/en-us/tech-zone/design/. The old Citrix VAD LTSR 7.15 design handbook can also be downloaded from https://docs.citrix.com/en-us/xenapp-and-xendesktop/7-15-ltsr/downloads/Citrix%20VDI%20Handbook%207.15%20LTSR.pdf.
The design considerations analyzed in the following sections are based on the official Citrix VAD design decisions, as listed in the Citrix Tech Zone and the Citrix VDI design handbook.
General design considerations
Pre-design checks
Firstly, it is important to determine if you have a single-tenant or multi-tenant Citrix Service Provider (CSP) implementation. Secondly, it is important to determine if the Citrix implementation will be an on-prem, cloud or hybrid implementation. In the case of cloud and hybrid implementations, one or more Citrix Cloud services will be included in the design. Thirdly, choosing the correct Citrix VAD version branch (Long Term Service Release LTSR vs Current Release CR) is of paramount importance in terms of product support lifecycle and feature availability. Based on these preliminary decisions, a proper reference architecture must be chosen from the Citrix Tech Zone as the baseline of the overall design. Creating bespoke (custom) architectures is inevitable, as no two infrastructures are ever going to be the same. If incorporating an on-prem infrastructure in a purely on-prem or hybrid implementation, gaining early insights and a deep understanding of the on-premise architecture is vital when making design decisions about availability, performance, capacity and security.
If you are a Citrix Service Provider (CSP) and wish to implement a multi-tenant Citrix VAD environment, refer to the following reference architectures: https://docs.citrix.com/en-us/tech-zone/toc/by-product/citrix-service-providers. Otherwise, if you are implementing Citrix VAD for a single tenant (enterprise mode installation instead of CSP), refer to the following reference architectures. Each architecture is differentiated based on the primary design desicision of whether or not to include Citrix Cloud services. If you will be using Citrix Cloud, is important to choose between Citrix Cloud VAD service vs. Citrix VAD Standard on Azure vs on-premises: https://docs.citrix.com/en-us/tech-zone/design/reference-architectures/citrix-managed-desktops.html.
Important note:
If your preliminary design involves a Citrix Cloud (DaaS) or hybrid implementation, ensure that you review the following resources first about Citrix DaaS reference architectures and design guidance.
- https://docs.citrix.com/en-us/tech-zone/toc/by-product/citrix-daas/reference-architectures
- https://docs.citrix.com/en-us/tech-zone/toc/by-product/citrix-daas/design-guidance
Before you start the actual Citrix VAD design, you need to ensure that you have assessed the following aspects in your customer's existing (source) and desired (target) environment.
- Define your organization (architecture, physical zones and data centers)
- Define the user groups (departments and users who will be running hosted apps and desktops)
- Define the applications (all types of application hosting)
- Define the project team (architects, systems engineers, application owners, developers, helpdesk agents)
Microsoft service dependencies
Citrix VAD is a Windows Communication Foundation (WCF) software solution, developed in the .NET framework. It has a heavy reliance on the Windows Server operating system, on .NET and on various Windows Server roles, features and services. A series of Microsoft server roles are required inside an Active Directory domain, as described in a separate article. Active Directory is the primary authentication store (identity provider) for Citrix VAD. All Active Directory domain and forest design considerations must be made early on before proceeding with a Citrix VAD solution, including supplementary Windows Server roles such as DNS, DHCP, TFTP, Certificate Services, Federation Services, File Server and SQL Server.
Citrix layered design methodology
The following sections assume that all Citrix VAD design concepts and components follow the Citrix layered design methodology, comprising the following layers.
- User layer
- Access layer
- Resource layer
- Hardware layer
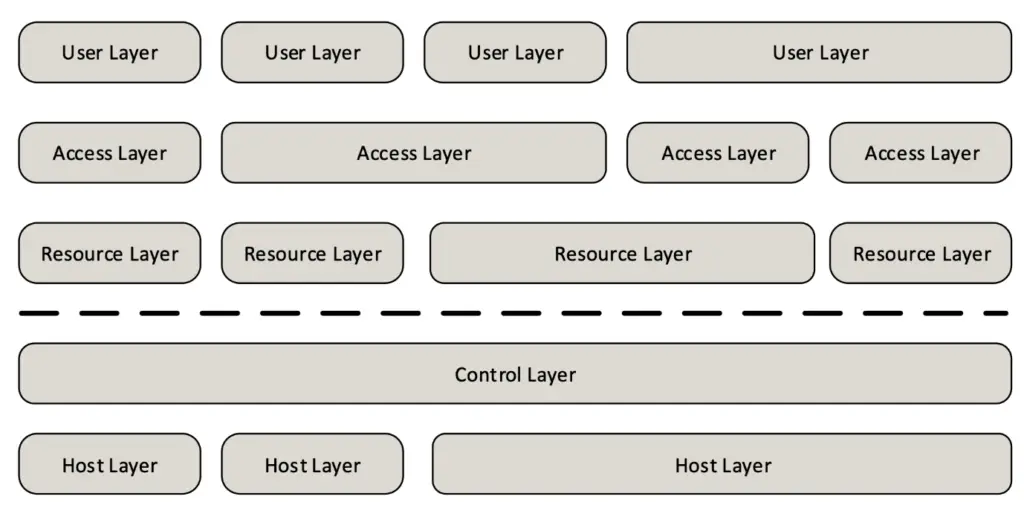
User layer design considerations
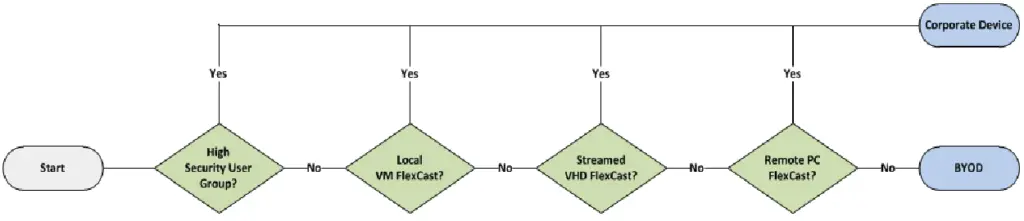
User device ownership and form factor
First off, you need to decide who is going to own the computing devices in your organization used to access the Citrix VAD sites and zones and also what types of devices will be used. There are generally two types of devices, either corporate-owned or user-owned, also known as Bring-Your-Own-Device (BYOD). The following flow diagram by Citrix helps us determine what type of device to use for each user group, depending on their requirements. Users can bring mobile devices (mobile phones, tables, laptops) or have desktop devices and thin clients.
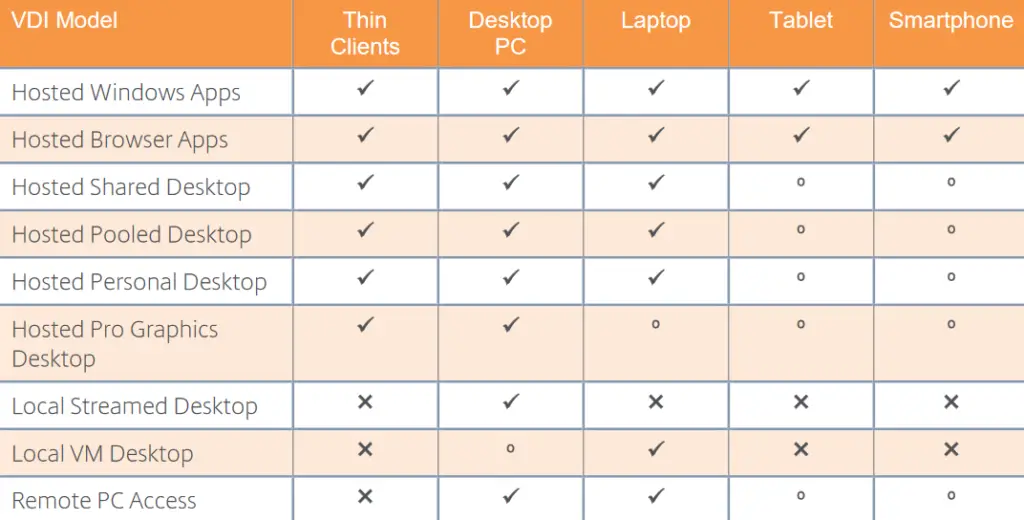
Depending on the Citrix VDI model, the following device form factors are supported, as shown in the Citrix table.
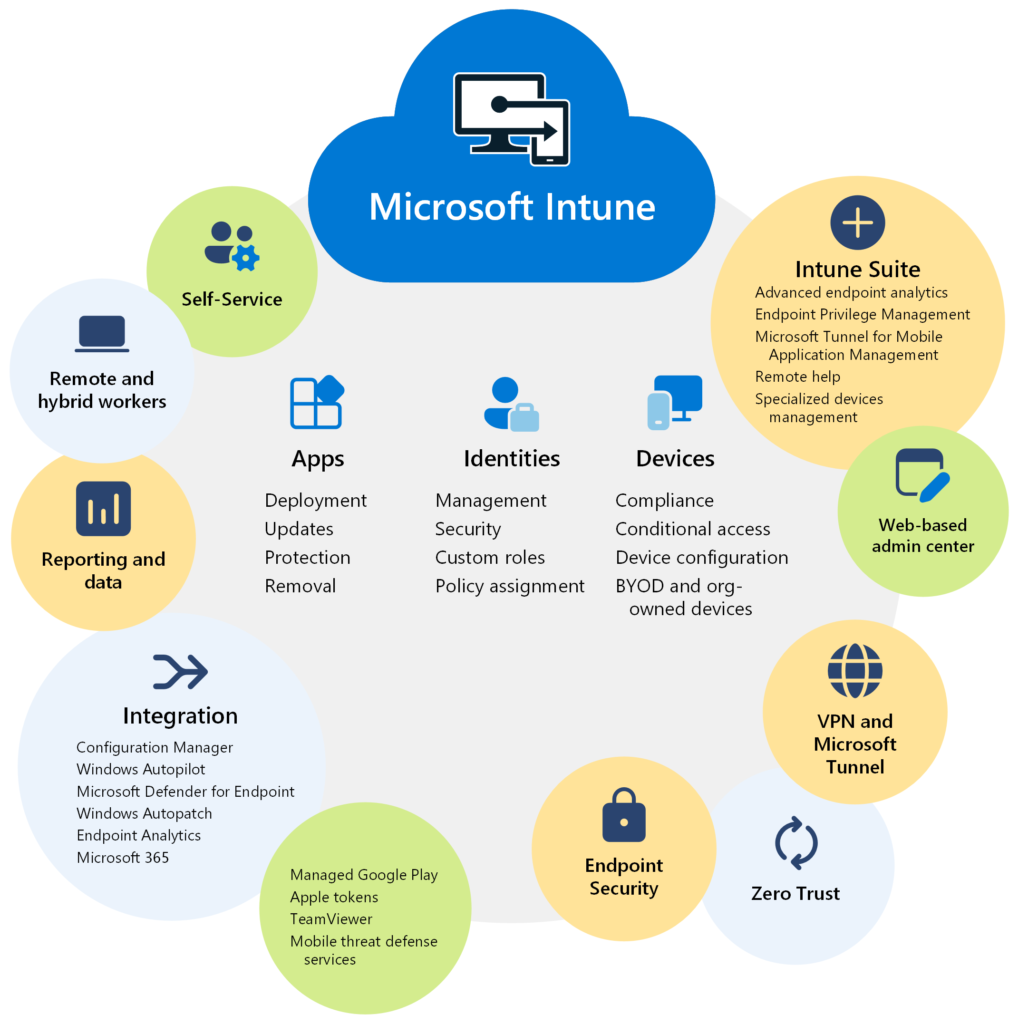
Mobile Endpoint Management (MEM)
MEM covers both mobile device management and mobile application management strategies and policies. You may need to consider using Citrix Endpoint Management or a third-party solution, such as Microsoft Intune. The following high-level architecture diagram provided by Microsoft Intune depicts the concepts and components involved in a MEM implementation.
Citrix Workspace App deployment options
Citrix Workspace App is the Citrix client application which allows for Citrix hosted desktops and apps to be launched by remote users. Citrix Workspace app supports a wide range of operating systems and devices and can be downloaded and manually deployed on any device from https://www.citrix.com/downloads/workspace-app/. For a large installation base however there are other automated methods available for deploying Citrix Workspace app. The following Citrix table summarizes these options. Each option is applicable to a number of target end-user devices.
In some cases, you may also need to consider a clientless option by using the Citrix Workspace App for HTML5 client. Citrix Workspace app for HTML5 enables users to access virtual desktops and hosted apps from a web browser.
Citrix Workspace app comes in both an LTSR and a CR release (current release). A detailed comparison of features available in each operating system's client version, including the Citrix Workspace App for HTML5 is provided by Citrix in the following article.
https://docs.citrix.com/en-us/citrix-workspace-app/citrix-workspace-app-feature-matrix.html
The initial configuration of Citrix Workspace App can either occur manually or via an automation method. The following table provides a summary of the initial configuration automation methods for Citrix Workspace App.
- Email-based discovery. Email based discovery requires Citrix StoreFront as well as an SRV DNS record which points to the FQDN of the StoreFront server. For remote access, NetScaler Gateway must be utilized with the corresponding SRV record in external DNS. A valid server certificate on the NetScaler Gateway appliance or StoreFront server must be present in order to enable email-based account discovery.
- Group Policy. Make use of the Citrix-provided admx template to set the StoreFront Account List option.
- Provisioning file. This file can be exported from the Citrix Storefront MMC console. The file is saved with a “*.cr” extension and can then be placed on a shared network resource, a Receiver for Web site, or other web-based resource or emailed to users.
- Citrix Studio. It is possible to set the StoreFront address via the properties of the Delivery Group.
Another Citrix Workspace App consideration is the client software update mechanism. Citrix Workspace App provides an autoupdate mechanism which can be switched on or off during and after installation.
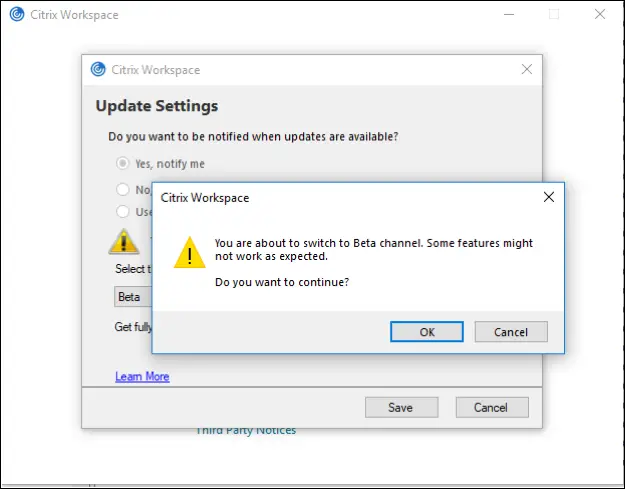
An alternative approach is to disable the native autoupdate feature and use a third party Enterprise software deployment (esd) tool, such as Microsoft System Center Configuration Manager (SCCM) to perform automated updates.
Last but not least, you may need to consider a series of plugins to be installed on top of Citrix Workspace App to add functionality to the client. A few plugin examples include the Citrix Gateway and the HDX realtime media engine for Skype for Business.
Access layer design considerations
Site and zone architecture design
Each customer has different business and technical requirements. The Citrix VAD architecture design is the first step in a series of assessment and design steps towards the final project implementation. It all starts by assessing the customer's current situation (as-is analysis) as well as their business and technical drivers for a Citrix VAD implementation. You may have a green field project (new deployment) or a brown field project (migration or upgrade or other types of integration work on an existing deployment). Ensure that you review the technical assessment templates available in this blog's free downloads section and use these templates to document the customer's IT infrastructure as well as document their business and technical requirements.
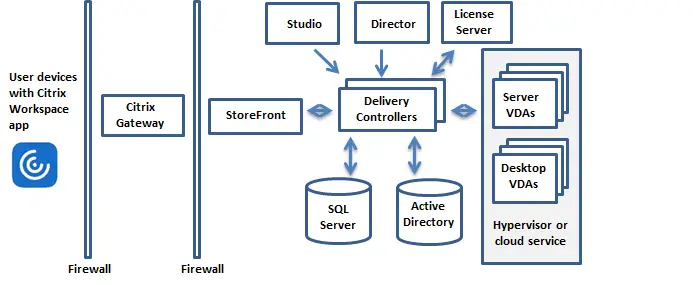
The fundamental Citrix VAD architecture is shown in the diagram below. This diagram shows all fundamental Citrix VAD components, laid out from left to right as the external (Internet) or internal traffic flows from the end user to the Citrix Virtual Delivery Agent (VDA) machines, where the hosted apps and desktops reside.
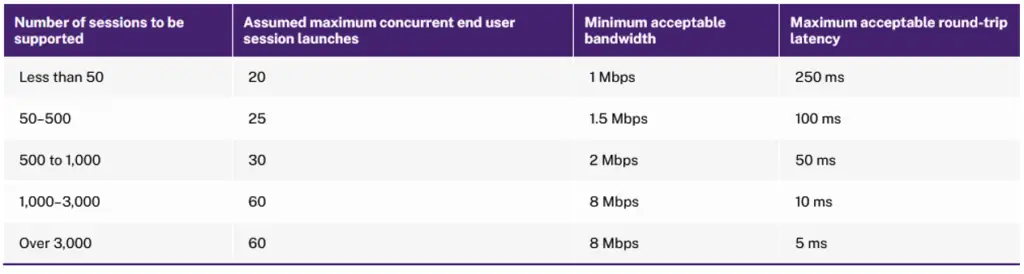
An early design decision about your architecture, after sizing your customer's user and workload requirements, is how many physical locations your Citrix VDA solution will comprise. This means that you will have to decide how many Citrix VAD sites and how many Citrix VAD zones you will create, based on your customer's geographical locations and available datacenters. Usually, the basic criterion based on you which you decide about site creation is the maximum acceptable latency between two zones. If the RTT latency is more than 250 ms, then you should choose to create a new VAD site rather than another zone. Also, depending on the total number of users and maximum number of concurrent sessions which each zone will need to accommodate, there are minimum network bandwidth requirements between the primary and each satellite zone. The minimum bandwidth requirements between the primary and each satellite zone can be referenced in the below table provided by Citrix.
Using the Citrix connection quality indicator and the Remote Display Analyzer tools is also a good idea. The Citrix Connection Quality Indicator (CQI) is a tool that notifies users of changes to user experience. It serves the following purposes:
- Assist users by pointing out issues that degrade the user experience.
- Provide real-time data for sophisticated users to find causes for lags in screen refreshes.
- Reduce the number of calls to help desks related to user experience issues.
Remember the basic VDA to Controller registration rules, i.e. primary zone VDAs never register to satellite zones and satellite zone VDAs can register to primary zone Controllers only if all their local zone Controllers fail. After deciding upon sites and zones, you will need to decide which components to install in each site and zone, including delivery controllers, storefronts and VDAs.
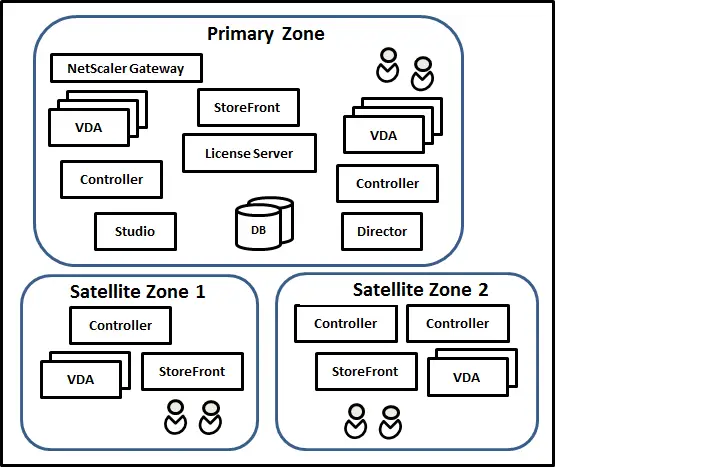
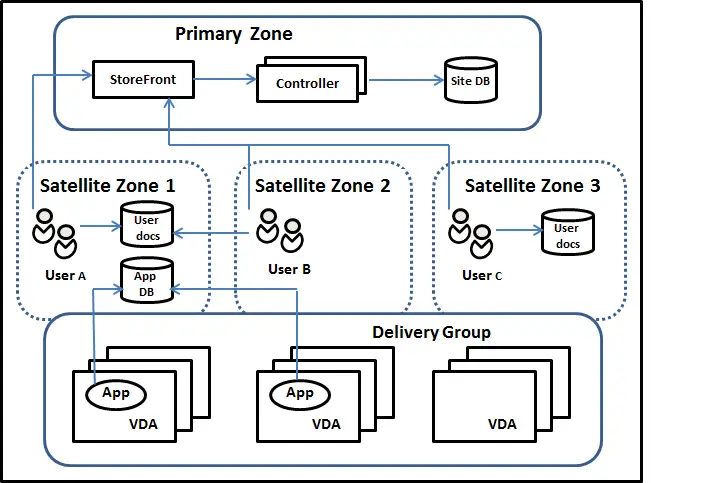
You also need to consider that Delivery Groups with hosted apps and desktops are spanned across multiple zones. One common consideration for each hosted app and desktop is the home zone. Usually an application's home zone should be the zone hosting the applications data/database, as shown in the example Citrix diagram below.
Disaster recovery (DR) planning
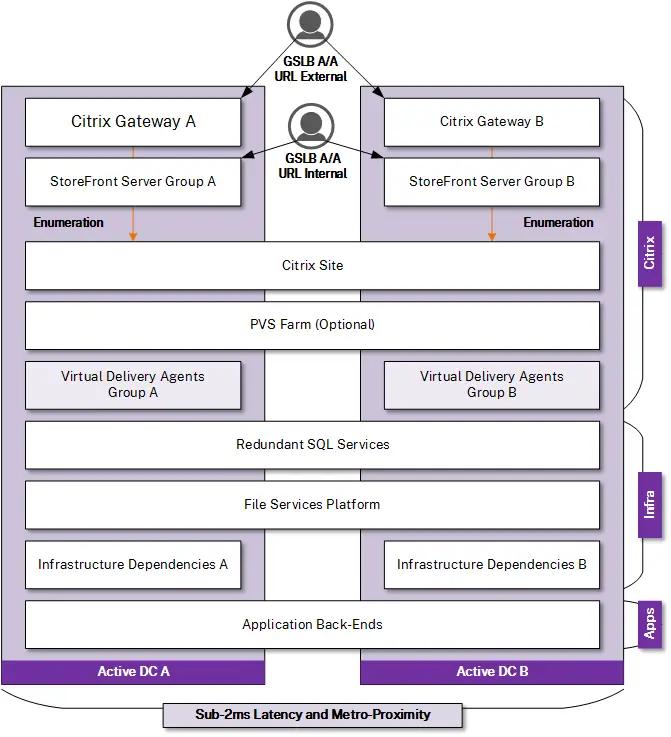
You need to define at an early stage if you are going to have two Active-Active or Active-Passive Citrix VAD datacenters in different physical locations. If you have such as a multi-site scenario, you should strongly consider placing at least one Citrix Netscaler (ADC) appliance in each site with Global Server Load Balancing (GSLB) configured with health monitors to the various Citrix server roles running on the primary site. This will allow for an active-active or active-passive DR scenario with manual or automatic failover.
Designing a disaster recovery solution (hot, warm or cold DR site) is not a simple endeavor as it encompasses a series of complex design decisions (RTO, RPO, application and data replication) and configurations. Paying special attention to critical server roles such as Active Directory domain controllers and understanding how to properly replicate traffic between the main the DR site is of high importance.
You can refer to the following Citrix best practice guides when designing your Citrix VAD DR architecture.
- VDI and DaaS Disaster Recovery Planning
- https://docs.citrix.com/en-us/tech-zone/learn/tech-briefs/business-continuity
- https://docs.citrix.com/en-us/tech-zone/design/reference-architectures/daas-for-business-continuity
The Citrix Netscaler components (Citrix Gateway) will need to be installed where needed, to ensure optimal routing. The Citrix Storefront Optimal HDX Gateway routing feature can assist in routing each connection request via its geographically closest Citrix Netscaler component. The Global Server Load Balancing (GSLB) component can assist in active-active Citrix VAD topologies with minimum of two sites.
After the disaster has been restored, re-routing traffic from the DR to the primary site involves the following tasks.
- Block access to the DR data center
- Terminate/drain existing sessions in the DR data center
- Complete data replication to the primary data center
- Configure replication back to the DR data center
- Enable access to the primary data center
It is critical to test your DR plan and revise it when any component of your architecture changes.
Netscaler and Storefront design considerations
The Citrix Netscaler ADC appliance is a L7 Network Virtual Appliance (NVE) which provides various services for routing, firewalling, NAT, switching, load balancing, vpn connectivity, caching acceleration and ICA reverse proxy (Citrix Gateway). It is available in various form factors and versions on-premise as well as Citrix Gateway service in Citrix Cloud. The Citrix Storefront component on the other hand is a front-end component running on IIS Web server and offering a series of server groups, storefront stores, Receiver for Web sites and the subscription and wallet services. It can also serve as an authentication point and work with Citrix Netscaler to allow access to both internal and external users. The following table provided by Citrix assists in defining the proper authentication points in your Citrix infrastructure.
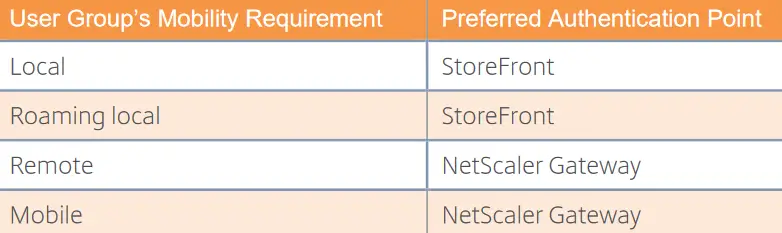
Each of the two possible authentication points (Netscaler and Storefront) provides its own authentication methods, as outlined in the following Citrix table.
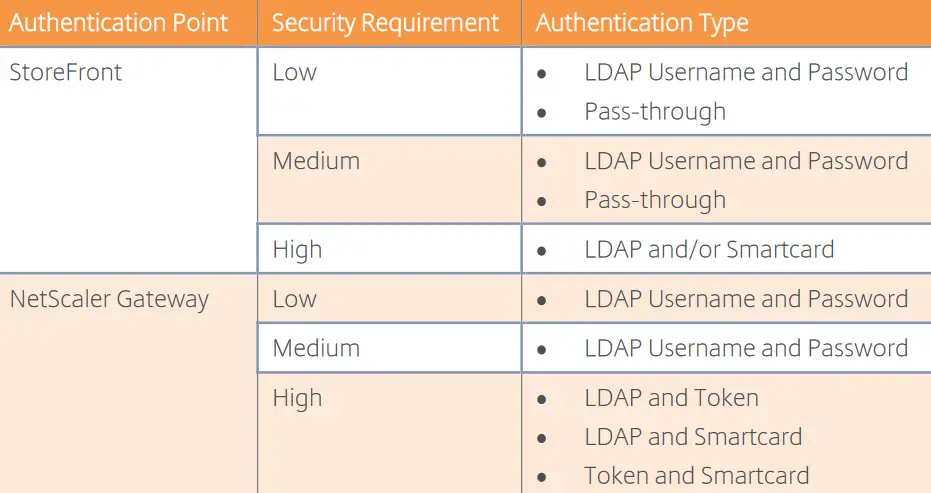
In certain more complex scenarios, you may need to consider authentication options such as Microsoft Entra Connect hybrid identity and the Citrix Federated Authentication Service for single sign on (SSO) and federation options. You should also consider the following Citrix Storefront features, depending on your implementation scenario:
- Optimal gateway routing
- Storefront store types and store options (e.g. anonymous stores)
- Receiver for Web site branding options
- Kiosks and storefront authentication device configured via powershell
- Multi-site aggregation
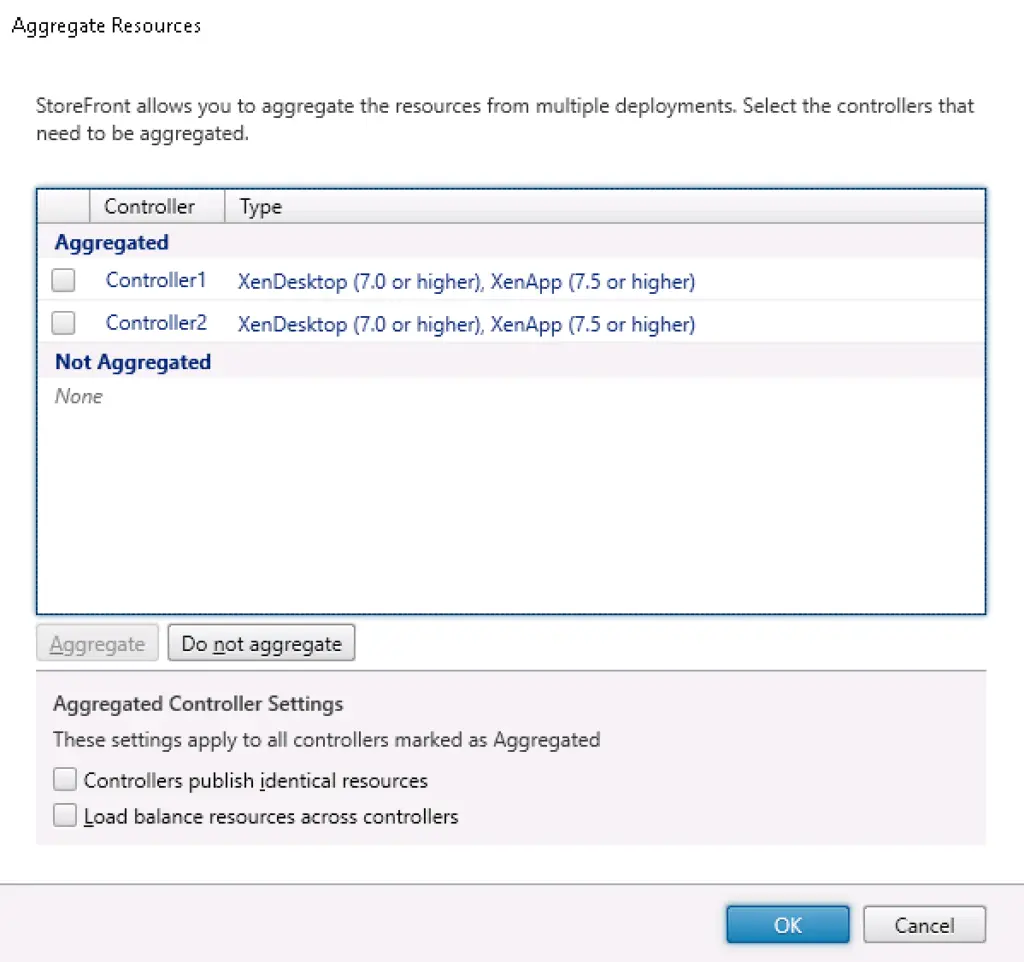
- Multi-site stores and synchronization options
- Application home zones
- Using single storefront group with multiple stores (cost-effective option) by configuring the Storefront subscriptions store service.
Designing Citrix Netscaler as per Citrix best practices involves the following decision areas:
- NetScaler Routing, Default Routes, Interfaces and Channels, VLANs, and GARP (https://support.citrix.com/article/CTX226652)
- Common Netscaler network topologies (One arm vs two arm: https://docs.netscaler.com/en-us/citrix-adc/current-release/getting-started-with-citrix-adc/network-topologies.html)
- Networking and VLAN Best Practices (https://support.citrix.com/article/CTX214033)
- VLAN types (https://support.citrix.com/article/CTX236843)
- NAT (https://docs.netscaler.com/en-us/citrix-adc/current-release/networking/ip-addressing/configuring-network-address-translation.html)
- https://www.carlstalhood.com/netscaler-essential-concepts-part-1/
- https://www.carlstalhood.com/netscaler-essential-concepts-part-2/
- https://discussions.citrix.com/topic/391315-netscaler-design-and-best-practices-handbook/
- https://docs.citrix.com/en-us/citrix-adc/13/networking/ip-addressing.html
- Citrix Netscaler Tech Zone https://docs.citrix.com/en-us/tech-zone/toc/by-product/citrix-networking
Integrating Citrix Storefront with Citrix Netscaler (Citrix Gateway) is of utmost importance. You will need to take the following design principles into account:
- Gateway URLs, Call back URLs, and GSLB URLs
- Default Appliance
- Optimal HDX Routing
- Beacons
More details about Storefront to Netscaler integration can be found at: https://docs.citrix.com/en-us/tech-zone/design/design-decisions/storefront-gateway-integration
Resource layer design considerations
Delivery Models and User Access
A Citrix Virtual Apps and Desktops solution can take on many delivery forms. The organization’s business objectives help select the right approach as the different models impact the local IT team’s management scope. Learn how Citrix Virtual Apps and Desktops management scope changes based on using a locally managed deployment, a cloud service deployment and a cloud managed deployment. A detailed comparison among the available Citrix VAD delivery models can be found at: Delivery Model Comparison. Also refer to the following article for details about the application delivery methods: https://docs.citrix.com/en-us/tech-zone/design/design-decisions/application-delivery-methods.
The following Citrix diagram provides a comparison of the available delivery models for Citrix VAD.
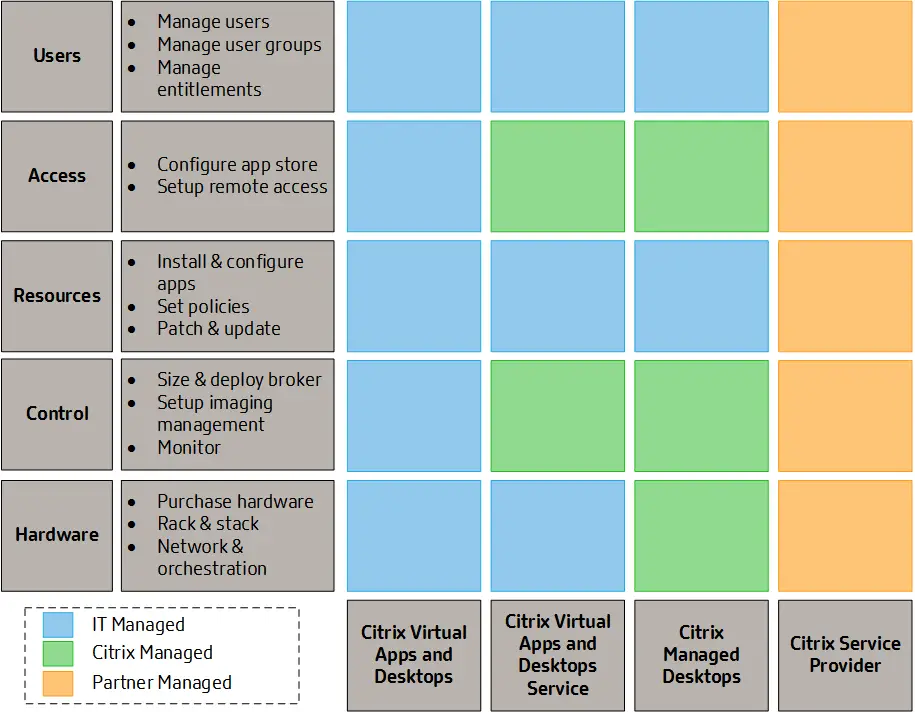
This is similar to the Microsoft Azure Shared Responsibility model.

VDI Models
Citrix VAD provides the following VDI model options: https://docs.citrix.com/en-us/tech-zone/design/design-decisions/vdi-model-comparison.
- Hosted Apps. Hosted apps include a few variants:
- Windows Apps
- VM hosted apps
- Linux Apps
- Browser Apps
- Shared Desktop
- Pooled Desktop
- Personal Desktop
- Pro Graphics Desktop
- Local Streamed Desktop
- Local VM Desktop
- Remote PC Access
The following Citrix table acts as a decision matrix when choosing the most appropriate Citrix VAD VDI model, depending on your implementation identified virtual desktop and virtual app workloads and mobility, personalization, security and criticality requirements.
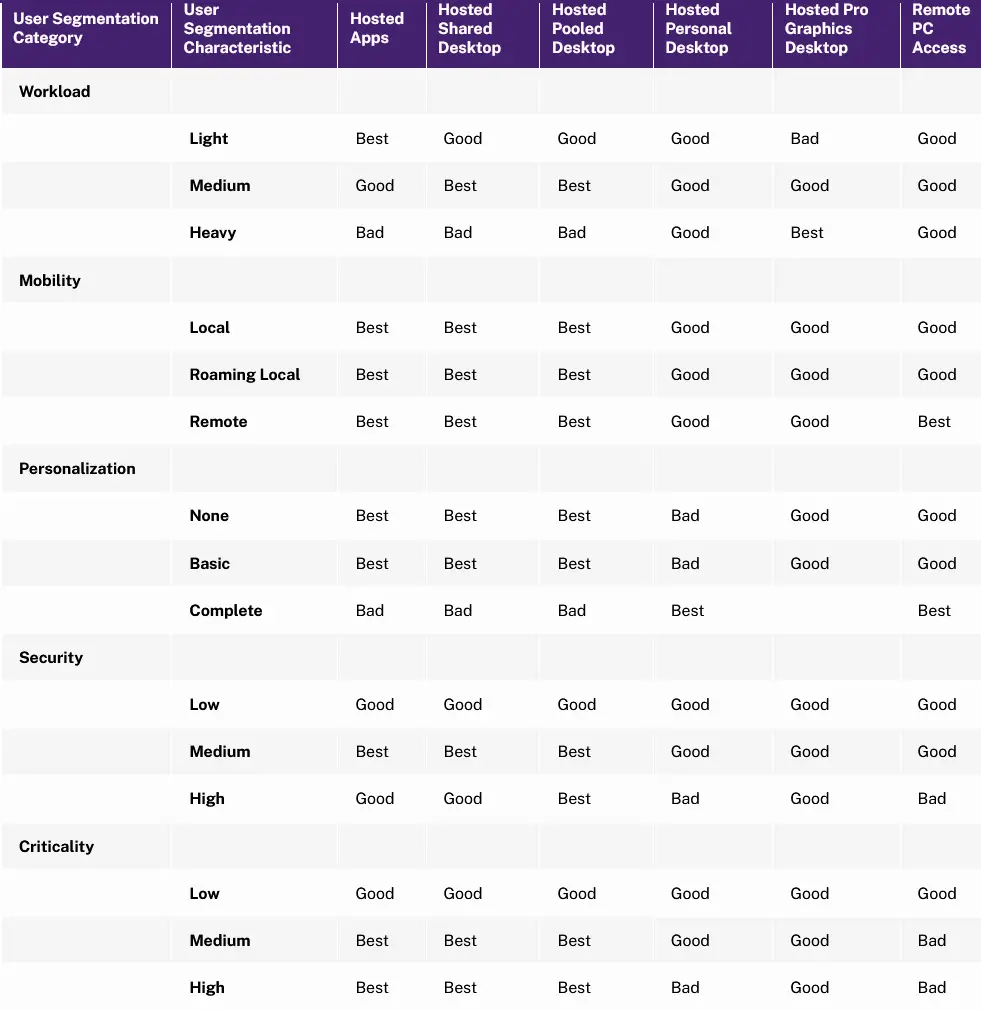
Image provisioning and management
The major image provisioning options for a Citrix virtual apps and desktops deployment are the following:
- Manual provisioning
- Machine Creation Services (MCS) (with or without App Layering)
- Citrix Provisioning (PVS) (With or without App Layering)
A discussion of Citrix App Layering benefits and design considerations can be found at https://docs.citrix.com/en-us/tech-zone/design/reference-architectures/app-layering. The below Citrix flow chart provides a decision flow for MCS vs PVS.
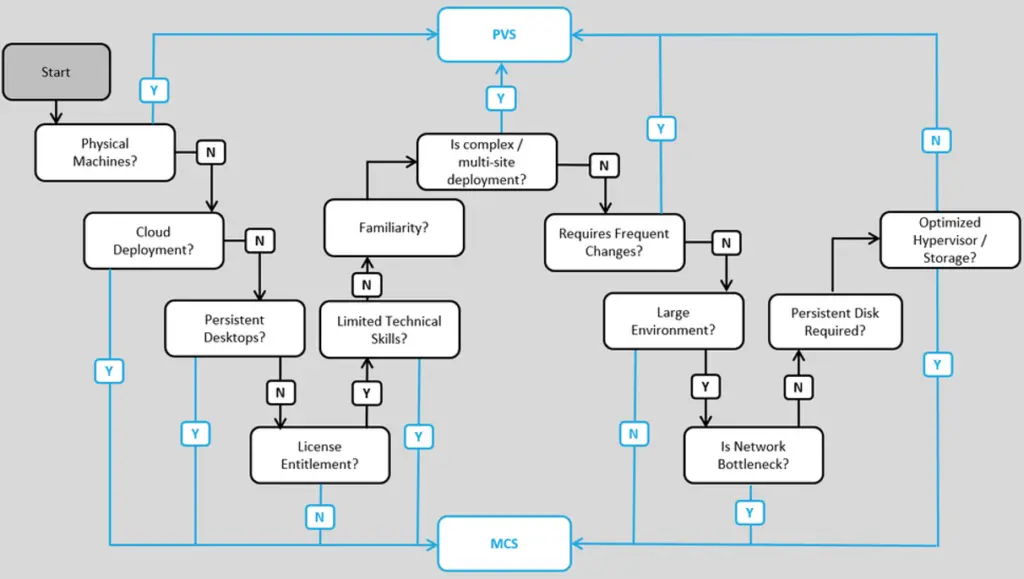
Hosted application optimization
Microsoft 365 and hosted application best practices
Citrix provides a series of best practice recommendations for optimizing operations of the Microsoft 365 apps, including Outlook, Teams and Onedrive for Business. Review more in the following articles.
- https://docs.citrix.com/en-us/tech-zone/build/deployment-guides/microsoft-365-citrix
- https://docs.citrix.com/en-us/tech-zone/learn/poc-guides/microsoft-teams-optimizations
Browsers
Ensure that you make use of the Active Directory Group Policy ADMX templates for customizing each browser's behavior inside Citrix by policy. Refer to both Citrix and Citrix CTP professional blogs for best practices from the field about how to optimize each known browser. Such as an example document is provided below for Google Chrome.
Deploying Google Chrome in a Virtual Desktop Environment
Control layer design considerations
Baseline policy design
The Citrix Baseline Policy Design article provides basic policy considerations for a Citrix VAD environment. Policies provide the basis to configure and fine-tune Citrix Virtual Apps and Desktops environments, allowing organizations to control connection, security, and bandwidth settings based on various combinations of users, devices, or connection types. It is important to consider the different methods by which you can configure Citrix and Windows policies in a Citrix VAD environment. These include the following:
- Citrix Workspace Environment Management (WEM)
- Citrix Studio
- Windows Group Policy Management Console (GPMC) based on .admx templates. To allow Citrix policies to be managed inside the GPMC, you will need to install the proper Citrix snap-in on all domain controllers. Also some Citrix components, such as Citrix Profile Management come with their .admx templates for AD group policy integration.
Group Policy Objets (GPO) should be organized per user and per computer policies. A single per-computer and single per-user GPO can be created for the Citrix VDA servers. Also you need to consider Citrix antivirus exclusions and security best practices for locking down hosted shared desktops while ensuring smooth performance of all Citrix services.
Also you need to take into account the policy precedence. Last but not least you should evaluate the usage of Active Directory group policy loopback processing in merge mode. This will allow you to apply user policies to Citrix VDA computer objects and therefore apply policies to Citrix users, based on which VDA machine they logon to.
The VDA power management policies are equally important. A good practice is to setup a reboot schedule for your server-OS VDA machines and determine your power policies for the single session VDA machines.
If you design to configure Citrix WEM to automate parts of your policy design, refer to the following Citrix best practice guide: https://docs.citrix.com/en-us/tech-zone/learn/tech-briefs/workspace-environment-mgmt.
Citrix Profile Management
Citrix Profile Management is a roaming profile solution and is configured via Active Directory Group Policy. Some of the most important Citrix profile management features to consider are the following:
- Active write-back. This feature is useful when multiple concurrent Citrix sessions (desktops, apps) are allowed for the same user. Active write-back dynamically synchronizes profile data between multiple sessions and the central user store (file server share) of the user's Citrix Profile. It also allows for dynamic synchronization in real-time from the user's local profile to the central user store immediately when there are changes in the user store. The default behavior (without active write-back) is that all changes are merged back to the central user store at user logoff. This can can creates issues in multi-session scenarios.
- Profile streaming. This is a useful feature which streams only the necessary Citrix Profile data at user logon, instead of all files and thus optimizes user logo times.
- Folder inclusion/exclusion. There are certain temp or cache data as part of an application's profile data, e.g. Web browsers, which can lead to profile bloat. It is important to explicitly include or exclude files and folders from Citrix Profile Management, as needed.
- Containerization of certain application's large profile data, such as Microsoft Outlook. Similarly to FsLogix profiles, Citrix profile management. You may need to consider Microsoft FsLogix free profile management solution (container-based) instead of the Citrix profile management solution (file and container based). FsLogix also supports multi-session scenarios.
Instead of roaming profiles, you may need to consider the Mandatory profile feature for some applications or users, if they need special folders and configuration to pre-exist inside the user's profile.
The shared storage (file server) on which the profile management solution stores the users' profile data can be either an on-prem Windows file server or another cloud solution, such as Azure Files PaaS service. Refer to my separate article about file server configuration best practices for profiles. The Citrix Profile Management with Azure Files article covers guidance and best practices for using Citrix Profile Management to manage user profiles on Azure Files as the back-end storage location. Best practices for Citrix Profiles in general are dependent on the Citrix VAD version used.
Another important consideration is how to configure a profile solution for multi-site deployments. In such cases, you need to decide between an active-passive and an active-active design. Using Microsoft DFSR is recommended for active-passive scenarios. The Citrix Profile Management user store path is a computer-level setting, meaning there can only be one path for every user that logs into a particular VDA. If you have different users with roaming profiles on different file servers, then you must use Active Directory user attributes and DFS namespaces to locate the user’s file server. The following diagram provides a list of options when constructing the UNC path to the Citrix user store, by using AD attributes, environment variables and profile management variables.
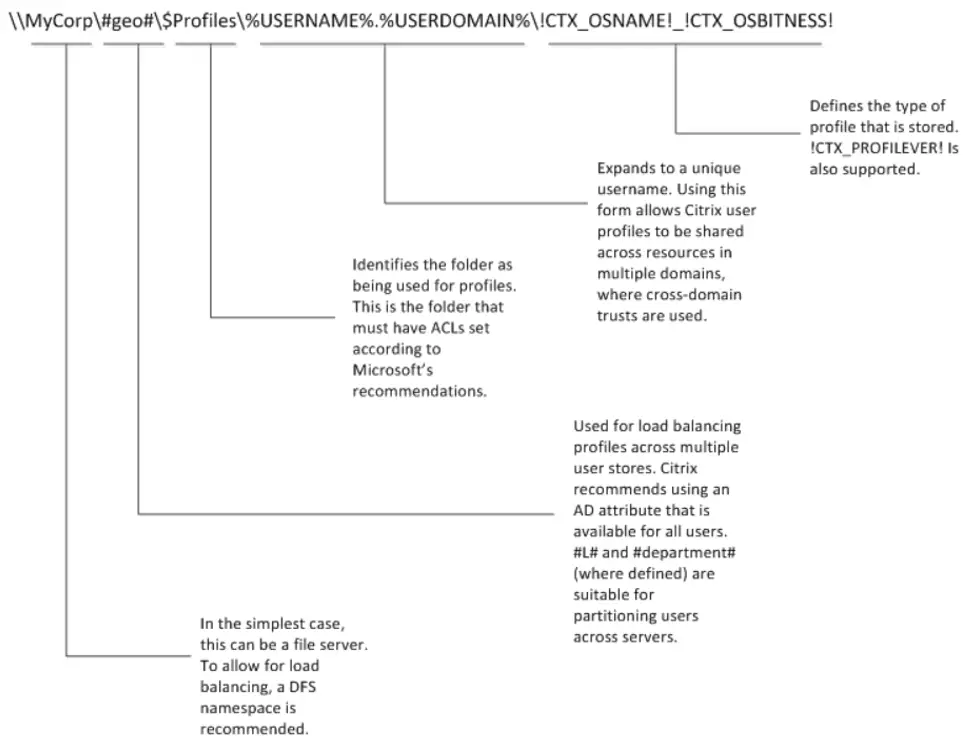
In active-active multi-site scenarios, Microsoft DFSR for roaming profiles is not supported, so another approach needs to be made. Refer to Carl Stalhood profile management article on Citrix active/active datacenter profile design recommendations.
Baseline Printing Design
The Citrix Baseline Printing Design article provides the basic pointers for Citrix printing design. Citrix Virtual Apps and Desktops supports various printing solutions. It is essential to understand the available technologies and their benefits and limitations to plan and successfully implement the proper printing solution. Some essential components to take into account in your design are the following:
- Auto-created client printers
- Session printers
- Universal print driver
- Universal print server
It is recommended to consult the following resource which is written by Citrix Architect Ban Van Kaam:
Content redirection design considerations
Citrix VAD utilizes a series of ICA virtual channels for each traffic type (data, voice/sound, images, video, printing, etc). The following Citrix diagram shows an overview of the Citrix VAD virtual channels.
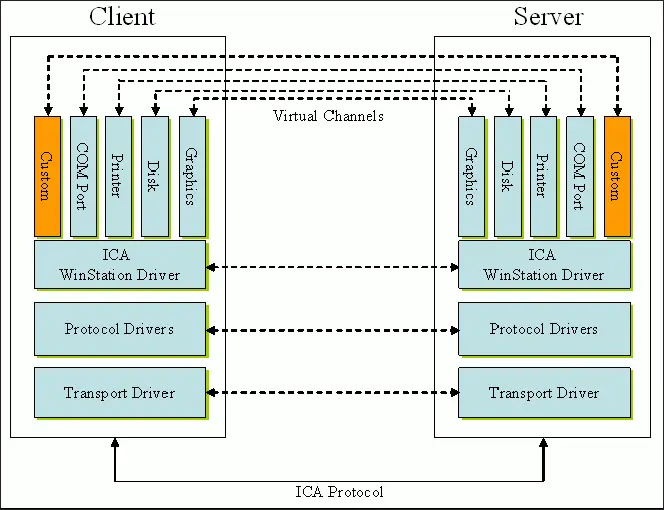
This section provides some design considerations about Citrix content redirection for all sorts of supported content.
USB redirection
The Citrix HDX-optimized printing virtual channel . It is recommended to use this channel for all your USB devices. If any legacy device cannot work with this ICA virtual channel, then using the generic USB redirection channel must be considered.
Folder redirection
Folder redirection is not a Citrix but rather a Microsoft operating system mechanism for "offloading" the users' files/data to a shared file server share, rather than including them into the user's roaming profile via Citrix profile management. Review my separate article on best practices for Windows file server folder redirection.
Clipboard redirection
The Citrix VAD "Client Clipboard Redirection" policy enables or disables "copy-paste" clipboard operations. The "Restrict Client Clipboard Write" and "Restrict Session Clipboard Write" policies control whether write access is enabled to the client clipboard and to the Citrix desktop clipboard respectively.
Also file copy paste between a local machine and a Citrix desktop or between Citrix desktops is controlled by the following policies. Copy and paste is achieved by using the right-click menu or keyboard shortcuts.
- To allow users to paste files from the VDA clipboard to the client, add the format CFX_FILE to the "Client clipboard write allowed formats" policy.
- To allow users to paste files from the client clipboard to the VDA, add the format CFX_FILE to the "Session clipboard write allowed formats" policy.
Sound redirection
Multimedia audio support and the various audio redirection Citrix VAD policies are discussed in the following article: https://docs.citrix.com/en-us/citrix-virtual-apps-desktops/multimedia/audio.html.
Web browser content redirection (BCR)
The Citrix VAD BCR feature offloads HTML resource rendering on the local Web browser instead of the browser running on the Citrix VDA. The following article describes how BCR works and its design considerations: https://docs.citrix.com/en-us/citrix-virtual-apps-desktops/multimedia/browser-content-redirection.html.
HDX 3D Pro
Citrix HDX 3D Pro supports DirectX and OpenGL and allows compatible hardware GPUs be passed through on an one-to-one mapping or be shared as vGPU resources in Citrix VDA machines. There are various design considerations when planning for HDX 3D Pro GPUs in both Windows single-session and multi-session operating systems.
Adaptive transport
Citrix adaptive transport is a data transport mechanism for Citrix Virtual Apps and Desktops as depicted in the following diagram.
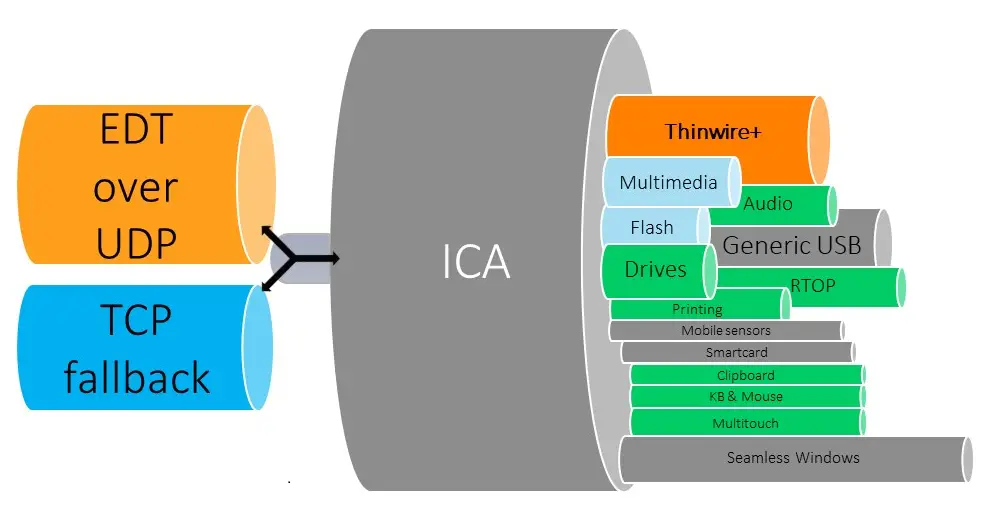
The following Citrix videos provide design guidance on setting up the components of Citrix adaptive transport, including adaptive display, adaptive throughput and adaptive transport.
For analysis of performance and graphics protocols you should use the Remote Display Analyzer (RDA). RDA is the easiest tool to analyze and change display protocol settings in any remote desktop services application (including Citrix VAD) on the fly.
Hardware layer design considerations
Scalability and capacity considerations
There are various benefits when using Citrix Hypervisor or any other supported hypervisor (HyperV or vSphere). Refer to the hypervisor documentation for more details. When designing the capacity of a hypervisor host server, you need to take into account the magic numbers for RAM memory and vCPU capacity. Citrix provides updated design recommendations about single server scalability (SSS), i.e. how many virtual machines and end-users a single hypervisor host can support, in the following article: https://docs.citrix.com/en-us/tech-zone/design/design-decisions/single-server-scalability.
The empirical magic multipliers are as follows. You can use these as a rule of thumb. Take the number of physical cores in a server, multiply it by 5 or 10, and the result will be your Single Server Scalability (SSS). You should also take into account special phyical core (pcore) features such as Intel Hyperthreading, which practically doubles the size of available logical threads. If you’re looking for the number of CVD VMs you can support, then you would use the “magic multiplier” of 5. If you’re trying to understand how many CVA users can run on a single piece of hardware, you’d use 10.
The magic number for RAM are some Citrix recommendations for the amount in vRAM to be provided to a VM, based on the anticipated workload of the end-user (light, medium, heavy). The following rough estimates are taken from the LTSR 7.15 virtual desktop design handbook.
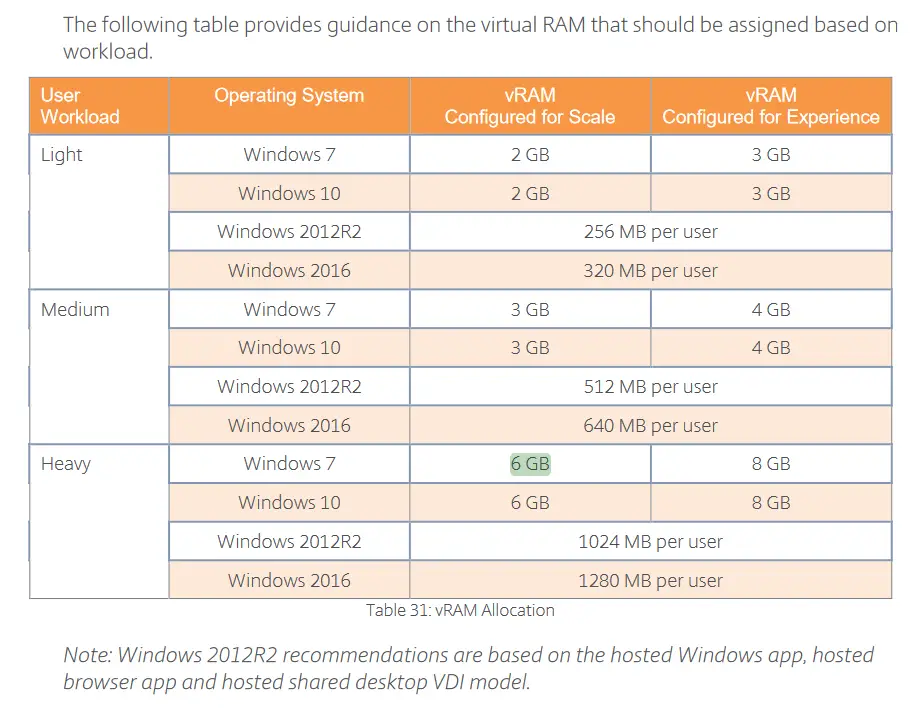
A N+x design should always be taken into account. That means that you should account for N+x physical hosts, where x are the number of physical hosts which, if destroyed and taken out of the infrastructure, will have no impact in the Citrix VAD operations. For example a N+2 design with 5 physical hosts, means that all hosted virtual machines can be served by only 3 of the 5 physical hosts if needed (3+2).
When designing server capacity for Citrix Cloud, the following metrics should be taken into account, to properly size VMs and Citrix Cloud capacity.
- x number of CVAD full time users (may save costs if users only need a desktop e.g. during 9:00-17:00 on a daily basis and not on a 24/7 basis).
- The Citrix desktops will be active x working hours per day, i.e. approximately y working hours per month. This corresponds to z full-time hours per week.
- All users have low Citrix hardware profile (task workers), i.e. all users are making light use of the Citrix VAD desktop. Task user profile assumes the following usage metrics:
- Expected IOPS: x
- Outgoing Bandwidth in kbps: y
- Storage Needs in GB: z
- Storage Redundancy: Geographic, GRS
- Windows 10 VDI: Yes
- VDI Type: Pooled
- Which Azure machines are you calculating (what are the machine types)? In most cases, the Azure D series is the best value for money option, which balances cost and performance.
- Standard MS pricing is assumed. If your customer has another Microsoft licensing agreement, this should be taken into account for the pricing estimations.
- All Citrix Cloud Resources will be deployed in the EU or other US region.
- All Azure resources (linked to Citrix Cloud subscription) will be deployed in the West Europe region.
- Azure geographic storage redundancy is assumed (GRS storage) for all Citrix Cloud components including the VDA servers.
- x GB of storage is assumed for each of the Citrix VAD infrastructure servers (all servers except for VDAs).
- y GB of storage is assumed for each Citrix VDA machine.
- All Citrix Cloud VAD server roles (except VDAs) will be using the Azure D2 v2 VM type.
- A highly available N+1 design approach must be assumed for the Citrix Cloud components.
More detailed capacity considerations for Citrix Cloud on Azure can be found at https://docs.citrix.com/en-us/tech-zone/design/design-decisions/azure-instance-scalability.
Network design considerations
Your core network must support 10 Gbps for all hypervisor hosts. This is particularly important in the case of Citrix provisioning (PVS) which is a network-intensive approach (as compared to Citrix MCS which is a storage-intensive approach).
You need to check if your implementation will have a Quality of Service (QoS) policy for the Citrix server roles and ensure that sufficient bandwidth is available to your servers and to your end users. The following table provides the results of Citrix bandwidth tests in a real environment with Virtual Apps and Desktops.
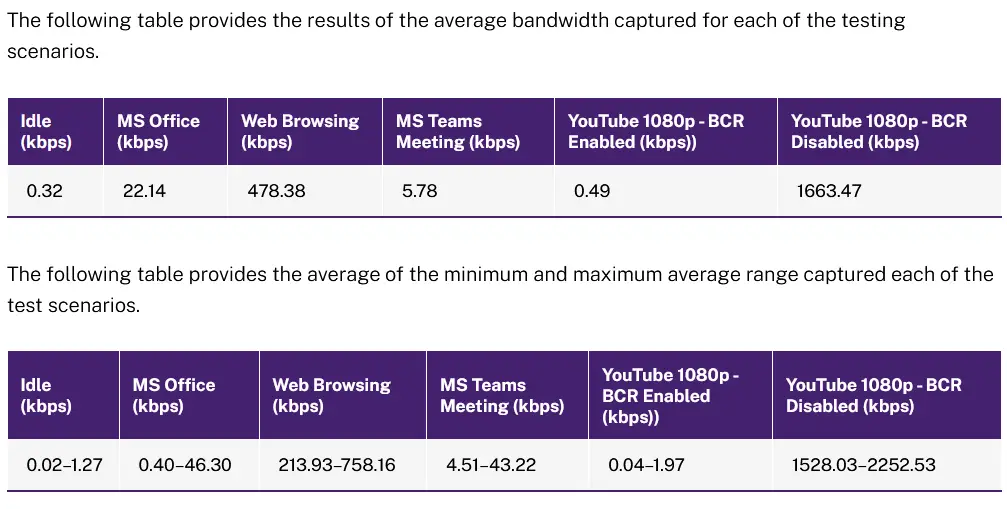
More details from the actual Citrix tests can be found at: https://docs.citrix.com/en-us/tech-zone/design/design-decisions/cvad-bandwidth-estimate.html.
An older mathematical formula for bandwidth calculations is also provided by Citrix as of 2014 (older versions of Citrix XenApp and XenDesktop).
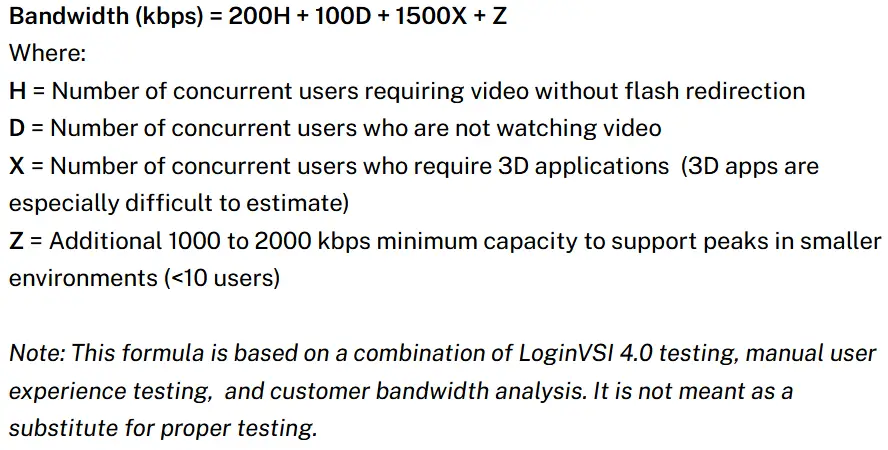
Testing tools such as LoginVSI can always provide more accurate guidance.
The following Citrix articles include detailed guidance and formulas for calculating acceptable bandwidth consumption estimations for various scenarios in Citrix XenApp and XenDesktop. Each user in XenApp and XenDesktop is modelled and organized into various user types, such as heavy HD video streaming or Autocad application worker or lightweight Internet browsing and office application worker. Printing also is a major factor which contributes to bandwidth consumption in XenDesktop user sessions.
- https://www.citrix.com/blogs/2010/05/20/how-much-bandwidth-do-i-need-for-my-virtual-desktop/
- https://www.citrix.com/blogs/2013/08/27/get-up-to-speed-on-xendesktop-bandwidth-requirements/
- https://www.citrix.com/blogs/2013/09/12/get-a-boost-with-xendesktop-bandwidth-optimizations/
- https://www.citrix.com/blogs/2014/04/16/from-the-field-xendesktopxenapp-bandwidth-update/
- https://www.citrix.com/blogs/2018/03/27/how-to-optimize-hdx-bandwidth-utilization/
- https://virtualfeller.com/2018/03/08/latest-xenapp-xendesktop-bandwidth-utilization-tests/
The following article (https://support.citrix.com/article/CTX133024) provides a very good analysis of softphone/VoIP integration with XenApp and XenDesktop. If the softphone installed in XenApp and XenDesktop does not belong to one of the major supported vendors (Cisco, Avaya, Vodyo), then the soft phone application should be running under the generic SIP over ICA configuration category. The various client-server software packages, such as the Citrix Realtime Optimization Pack for Skype for Business server optimize the end user experience. However additional Citrix technologies, such as the Adaptive Transport and EDT protocol help optimize the end user experience in terms of bandwidth and latency management.
When considering thin clients for XenApp and XenDesktop environments, the major consideration and decision point should be to determine if the thin clients are certified by the Citrix Ready program: https://citrixready.citrix.com/. Citrix recently released the "Workspace Hub" initiative which offers Citrix-ready thin clients supporting HDX RealTime Optimization Pack at low cost. Citrix works closely with Stratodesk and their NoTouch OS Desktop in order to provide old PC re-purposing and thin client utilization capabilities to customers.
Horizontal design considerations
This section provides a list of some non-functional aspects of your design which encompass the full breadth of the solution and affect all individual design factors mentioned in the previous sections.
Licensing and cost optimization
A Citrix VAD infrastructure requires the following types of licenses to be considered. The Citrix license server component is redundant by design in that any Citrix VAD solution can work up to 30 days without a license server. So having a single (standalone) Citrix license server is sufficient.
- Citrix VAD licenses (per-user/device or concurrent)
- Citrix Netscaler licenses (license server runs on the Netscaler appliance)
- Microsoft RDS licenses
- Windows Server operating system licenses (CPU core licensing, user CALs and external connectors)
- Windows client operating system licenses (Microsoft VDA license for VDA scenarios)
For Citrix Cloud costs, refer to the following official cost calculation resources:
- https://www.citrix.com/blogs/2022/01/26/daas-cost-citrix-calculators/
- https://www.citrix.com/products/citrix-daas/resources/azure-virtual-desktop-calculator.html#/
- https://www.citrix.com/products/citrix-daas/resources/citrix-azure-calculator.html#/
Fault Tolerance
Fault tolerance, also known as high availability (H/A) and resiliency, is one of the non-functional characteristics of a Citrix infrastructure which should be taken very seriously during the design phase. The following options should be considered for various components of your Citrix VAD solution.
- Load balancing, which comes in the form of hardware load balancing (HLB), DNS round robin or Windows Network Load balancing (NLB). Hardware load balancing via Citrix Netscaler or another third party solution is the recommended option.
- Citrix Local Host Cache (LHC) for the Citrix databases. If the Citrix databases go offline then the Citrix LHC component ensures that Citrix sites continue to run with a local SQL Server express installation on each Delivery Controller, which has a continuously replicated subset of information from the Citrix databases. Local Host Cache engages when the site database is inaccessible for 90 seconds. As of XenApp and XenDesktop 7.16, the connection leasing feature (a predecessor high availability feature in earlier releases) was removed from the product, and is no longer available. The following Citrix diagram presents how Citrix LHC works.
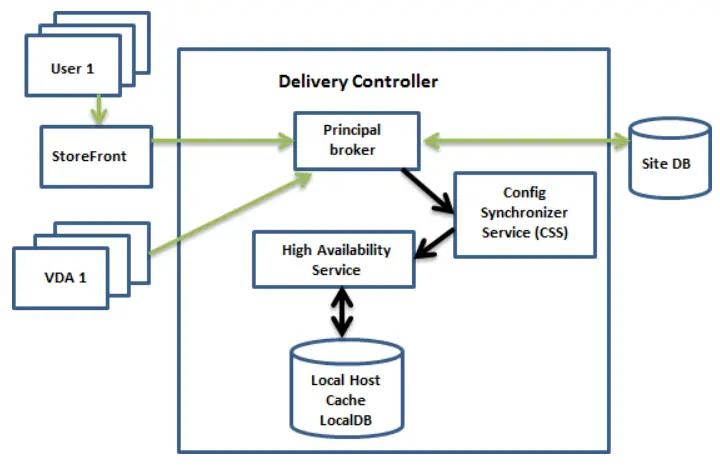
- Clustering, which comes in the form of either physical clusters (host clusters) or virtual clusters (guest clusters). An example of host clusters is the Citrix Hypervisor host clusters (pools) and an example of guest clusters is SQL Server active-passive cluster. Host clusters provide VM-level HA while guest clusters provide application-level HA.
- For active-active multi-site high availability considerations, refer to the ealier section of this article entitled "disaster recovery considerations.
Performance optimization
Various Citrix VAD performance optimization are discussed in the following article: http://docs.citrix.com/en-us/tech-zone/toc/by-product/citrix-virtual-apps-and-desktops/optimizations.
Security and Zero Trust
Assess the environment’s current security configuration and make necessary adjustments to bring in line with leading security practices. Refer to the following articles for details on how to secure a Citrix VAD and Citrix Netscaler environment.
- https://www.citrix.com/about/legal/security-compliance/security-standards.html
- https://docs.citrix.com/en-us/tech-zone/toc/by-product/security
- https://docs.citrix.com/en-us/tech-zone/build/tech-papers/cvad-security-best-practices
- https://docs.citrix.com/en-us/tech-zone/build/tech-papers/antivirus-best-practices
Your network design should be in-tune with the overall IP networking infrastructure where the on-premises solution will be hosted. Segregating your Citrix infrastructure into VLANs is an important decision. The firewall ports involved in all Citrix VAD communications are included in the following article: https://docs.citrix.com/en-us/tech-zone/build/tech-papers/citrix-communication-ports.
Performing a security hardening of your Citrix infrastructure mainly involves the following steps:
- Network VLAN design. This should be combined with network ACL whitelist rules, to only allow Citrix expected traffic.
- Including an endpoint antimalware solution, for both servers and workstations.
- Enabling Windows Server User Account Control (UAC) in all machines
- Perform security hardening of all your hypervisor master images, by consulting the CIS OS security templates. In the case of Citrix VDA, utilize the Citrix Optimizer tool to include the most common performance and security optimizations.
- For all servers, create a mixture of Citrix and Windows policies, all to be managed via the AD Group Policy Management Console, which contribute to the security hardening of the Citrix machines and more specifically the Citrix VDA machines. Create and apply any policy which may reduce the attack surface of a Citrix machine.
- Using Citrix Provisioning (PVS) with read-only VDA machines instead of manual provisioning limits the risk of a malicious end-user applying machine-wide changes.
- Encrypt all Citrix components' internal traffic. By default, all external (customer-facing) traffic is encrypted by default. Further traffic encryption configuration for Citrix internal traffic should take place, including for example the TLS security of Citrix Controller STA XML service traffic and Citrix Director or Citrix Netscaler HTTPS administrator consoles.
- Be mindful of your Citrix administrator RBAC roles, scopes, permissions and credentials. Use strong passwords and apply a password change policy. Utilize Windows Server managed service accounts and minize
- Utilize Citrix Federated Authentication in combination with Citrix Netscaler advanced AAA capabilities to configure at least two-factor authentication (2FA) for all end-user sessions via the Netscaler.
- Keep all your Citrix systems up-to-date at the operating system and application software and firmware update level.
- Subscribe to Citrix security bulletins to receive new release notes of security fixes to discovered security vulnerabilities (https://support.citrix.com/user/alerts).
If you are interested in employing Zero Trust Network Access (ZTNA) in your environment, refer to the Citrix Secure Private Access, which provides Zero Trust Network Access (ZTNA) to private web apps and SaaS Apps. Citrix Secure Private Access On-Premises is a customer-managed Zero Trust Network Access (ZTNA) solution which allows for VPN-less access to Internal web and SaaS applications. Secure Private Access provides the following features: least privilege principle, single sign-on (SSO), Multifactor Authentication and Device posture assessment, application-level security controls and app protection features, with a seamless end-user experience. The solution utilizes Citrix StoreFront on-premises and Citrix Workspace app to allow for seamless and secure access experience to access web and SaaS apps within Citrix Enterprise Browser. This solution also leverages the NetScaler Gateway to enforce authentication and authorization controls. More architectural details of the Citrix Secure Private Access on-premise solution can be found at: https://docs.citrix.com/en-us/tech-zone/build/deployment-guides/secure-private-access-on-premises. If you are interested for the Citrix Cloud Secure Private Access solution refer to the following guides instead: https://docs.citrix.com/en-us/tech-zone/toc/by-product/citrix-secure-private-access/reference-architectures.
Administrator roles and permissions
Always make use of the Citrix RBAC role and scopes and assign permissions ideally to AD security groups instead of individual users. Creating custom RBAC roles and scopes inside the Citrix Studio console is the best approach to least privilege access, as per the security best practices.
Monitoring, alerting and operations
When monitoring your Citrix VAD implementation, you should cater for various aspects such as the following:
- Windows updates and application updates
- Automation and orchestration. Running Citrix ADM for orchestrating Citrix Netscaler components and Citrix WEM for orchestrating Citrix VAD components is a good idea in many scenarios.
Running a Citrix VAD daily or weekly maintenance script is also a best practice and can minimize your overall administrative effort and daily helpdesk calls. A common Citrix maintenance script (Powershell, Ansible or other automation framework) would encompass the following repetitive tasks:
- Send notification to any active Citrix VAD users that a maintenance will be starting soon
- Set maintenance mode to on for all Citrix VDA machines
- Start logging off users from all or a subset of VDA machines
- Apply application updates to all Citrix servers
- Cleanup local profiles in all or a subset of VDA servers. This can cover both a Citrix Profile Management and FsLogix profile solution
- Reboot all or some Citrix VDA servers
- Check status up for all Citrix and "automatic start" Windows services in all Citrix machines.
- Run disk health check routines in all Citrix servers
- Apply latest Windows updates (security, monthly rollup and feature updates)
- Set maintenance mode off for all Citrix VDA servers
- Run Citrix Director application and desktop probes to simulate a successful desktop and app launch
- Send email notification to Citrix administrator team with the results of the maintenance script run along with the script's logs.
- Update any existing status pages of the Citrix VAD service state (down/up) as the maintenance is completed.
This Citrix periodic maintenance script can either be run manually or automatically in the form of a Windows scheduled task.
The following Citrix management consoles are available in an on-prem environment. Citrix Cloud has its own Web-based equivalent management consoles.
- Citrix Studio (MMC and HTTP Web-Studio in latest VAD versions)
- Citrix Director (HTTP)
- Citrix Storefront (MMC)
- Citrix licensing (HTTP)
- SQL Server Management Studio and Confiuration Manager (for Citrix VAD database management)
Citrix Analytics
It would be advantageous from an administrative effort perspective to deploy Citrix Analytics in your Citrix VAD environment, even if you are operating on-premises only. Refer to following design and implementation guides about Citrix Analytics: https://docs.citrix.com/en-us/tech-zone/toc/by-product/citrix-analytics.
It is advisable to run a proof of concept (PoC) before integrating Citrix Analytics to your on-premises environment. A detailed Poc guide is provided at https://docs.citrix.com/en-us/tech-zone/learn/poc-guides/performance-analytics.
Citrix SDKs and APIs
Several SDKs and APIs are available with the latest CR release of Citrix VAD. To access the SDKs and APIs, go to Build anything with Citrix (Citrix microsite for developers). From there, select Citrix Workspace to access programming information for Citrix Virtual Apps and Desktops and its related components. The Citrix Virtual Apps and Desktops SDK and the Citrix Group Policy SDK can be installed as a module or a snap-in. Several component SDKs (such as Citrix Licensing, Citrix Provisioning, and StoreFront) install using only a snap-in. For Citrix Netscaler, the Nitro Powershell API is available. As of Dec 2023, Citrix is gradually moving away from Nitro API into the new Netscaler next-gen API (HTTP REST): https://developer-docs.netscaler.com/en-us/nextgen-api/getting-started-guide.
Troubleshooting
You can refer to my e-book entitled "Troubleshooting Virtual Apps and Desktops" (https://www.amazon.com/Citrix-Virtual-Apps-Desktops-troubleshooting-ebook/dp/B08LJSYXGR) for a comprehensive approach to Citrix VAD troubleshooting. The Citrix Tech Zone diagrams poster for on-prem infrastructures in particular is an invaluable tool to help you understand the Citrix traffic flows and troubleshoot a Citrix environment more efficiently: https://docs.citrix.com/en-us/tech-zone/learn/diagrams-posters/virtual-apps-and-desktops. Such an example troubleshooting diagram is shown below.
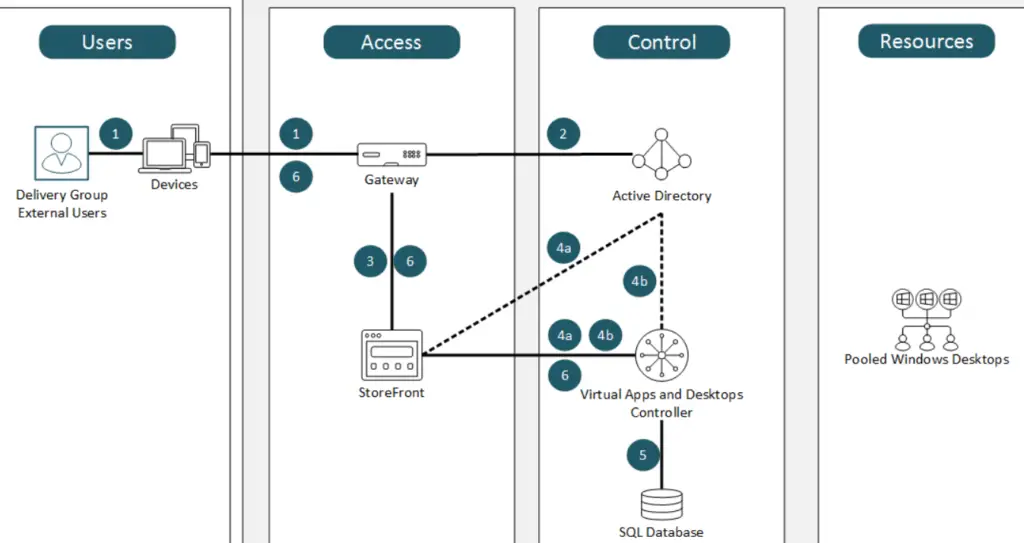
When troubleshooting Citrix VAD environments, it is important to maximize usage of all useful features of Citrix Director, including the proactive application probing features, as described in the following article: https://docs.citrix.com/en-us/citrix-daas/monitor/troubleshoot-deployments.
Additional design references
- https://www.amazon.com/Citrix-Virtual-Apps-Desktops-troubleshooting-ebook/dp/B08LJSYXGR
- CSP Reference Architecture – Virtual Apps and Desktops Service
- https://docs.citrix.com/en-us/tech-zone/design/reference-architectures/virtual-apps-and-desktops-service.html (for single tenant)
- Virtual Apps and Desktops Standard for Azure Tech Insights, Tech Briefs and Designs
- https://docs.citrix.com/en-us/tech-zone/design/reference-architectures/virtual-apps-and-desktops-azure.html
- https://docs.citrix.com/en-us/tech-zone/design/design-decisions/azure-instance-scalability.html
- https://www.carlstalhood.com/
