Case #
You need to assign one or more built-in policies in Azure Policy. This KB article provides guidance on how to assign built-in policies in Azure policy. The following list provides the most frequently utilized built-in Azure policies. This is not an exhaustive list but it provides an understanding of the breadth and depth of available built-in Azure policies.
- Allowed Locations: Enforces restrictions on the locations where resources can be deployed.
- Audit VMs that do not use managed disks: Audits virtual machines that do not use managed disks, promoting best practices for VM management.
- Allowed Virtual Machine SKUs: Restricts the usage of specific VM sizes or series based on your organization's requirements.
- Allowed Storage Account SKUs: Controls the types of storage accounts that can be created, preventing the use of unsupported or costly options.
- Audit Deployments with Public IP Addresses: Audits deployments that include resources with public IP addresses, promoting secure network configurations.
- Deny Public IP Creation: Blocks the creation of public IP addresses, enforcing a private network environment.
- Allowed Network Security Group Rules: Defines a set of allowed inbound and outbound network security group (NSG) rules to restrict network traffic.
- Audit Unencrypted Virtual Disks: Audits the presence of unencrypted virtual disks, ensuring data security.
- Allowed Diagnostic Settings Categories: Defines the allowed diagnostic settings categories for Azure resources to manage monitoring configurations.
- Audit Unattached Managed Disks: Audits the presence of unattached managed disks, helping optimize resource usage and cost.
- Allowed Virtual Network Service Endpoints: Enforces restrictions on the virtual network service endpoints that can be enabled.
- Deny Classic Virtual Networks: Prevents the creation of classic virtual networks, encouraging the use of Azure Resource Manager (ARM) model for network management.
- Audit Missing Tags: Audits resources that do not have specified tags, ensuring consistent tagging for resource management.
- Allowed Resource Types: Restricts the types of resources that can be deployed in your Azure environment.
- Deny Deployments without a Blueprint Assignment: Blocks resource deployments that are not associated with a defined blueprint assignment.
- Allowed Marketplace Offer Types: Controls the allowed Azure Marketplace offer types for resource deployments.
- Audit Security Center Recommendations: Audits compliance with Azure Security Center recommendations, ensuring security best practices are followed.
Solution #
This section provides a solution on how to assign built-in policies in Azure policy. To assign built-in policies in Azure policy, carry out the steps below. The below example refers to applying a sample built-in policy which restricts which Azure VM SKUs can be used when provisioning a new Azure VM via Azure ARM deployment methods, including the REST API, the Azure portal, Azure CLI, Azure Powershell, Azure Cloud Shell and Azure ARM JSON templates.
- Sign in to the Azure Portal (https://portal.azure.com/) using your Azure account.
- Navigate to the Azure Policy service. You can find it by searching for "Policy" in the search bar at the top of the Azure Portal.
- In the Azure Policy service, click on the "Definitions" tab in the left-hand menu.
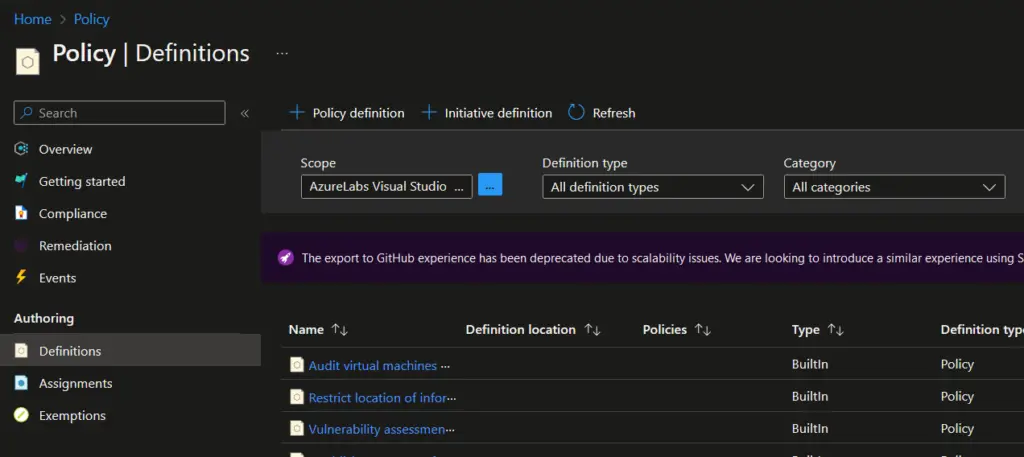
- In the "Definitions" tab, you can search for the specific policy you want to assign. In this case, search for "Allowed virtual machine size SKUs" and select the appropriate policy from the search results.
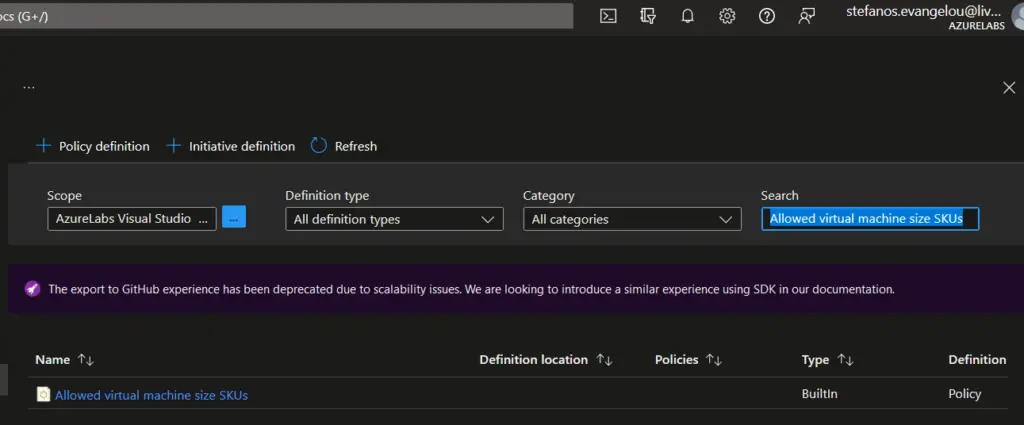
- In the policy details page, review the description and the parameters associated with the policy. Parameters allow you to customize the policy to meet your requirements, such as specifying the allowed VM SKUs.
- Click on the "Assign" button to assign the policy to a scope. A scope defines the scope of the policy enforcement, such as a subscription or resource group.
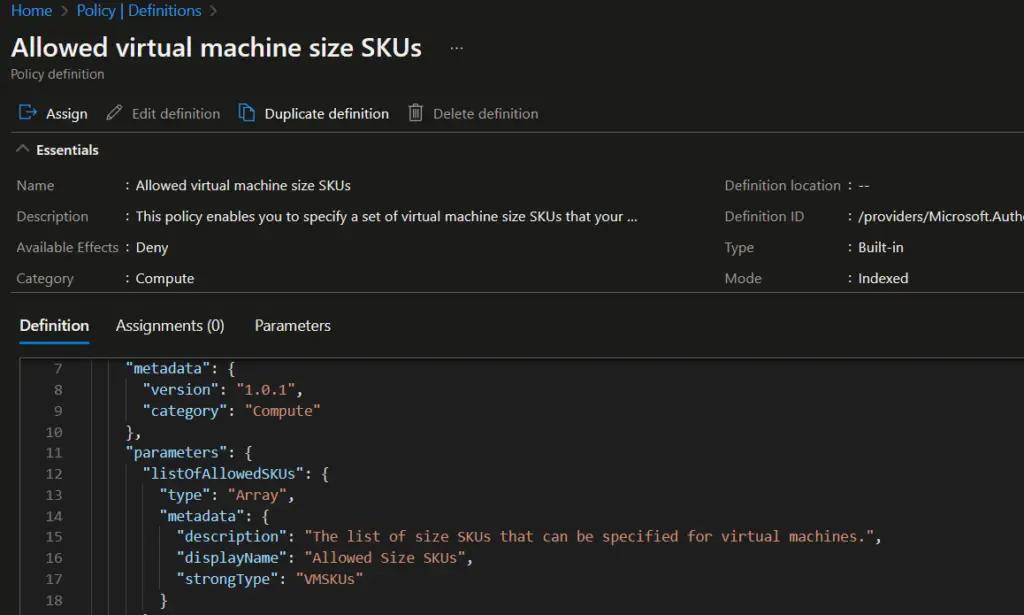
- In the "Assign Policy" page, select the appropriate scope where you want to enforce the policy. You can choose a subscription, resource group, or management group, depending on your requirements.
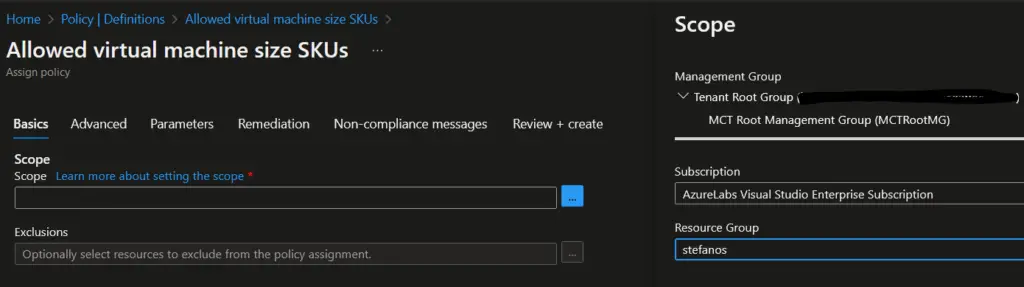
- Provide a unique name and optional description for the policy assignment.
- Configure the "Parameters" section based on the policy requirements. For the "Allowed Virtual Machine SKUs" policy, you may need to specify the list of allowed VM SKUs.
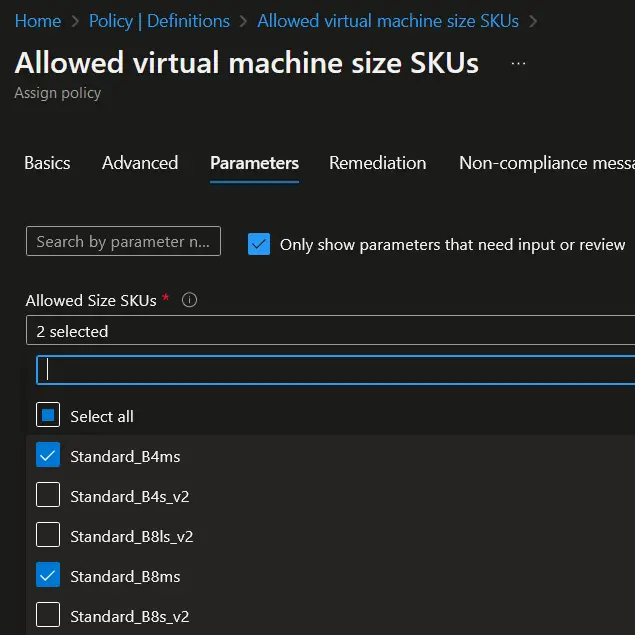
- Set the "Remediation" options.
- You can set a "Non Compliance message". This is an optional step.
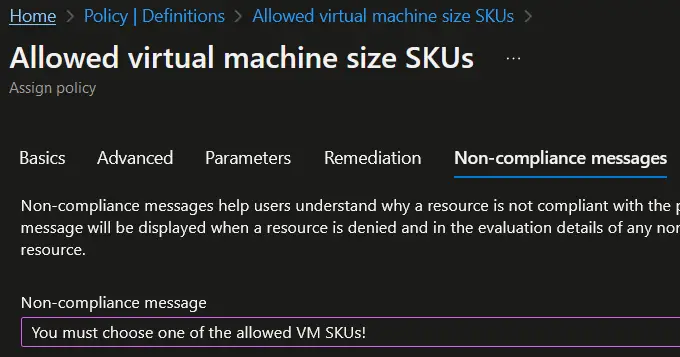
- Click on the "Review + Create" button, review the assignment details, and then click on the "Create" button to create the policy assignment.
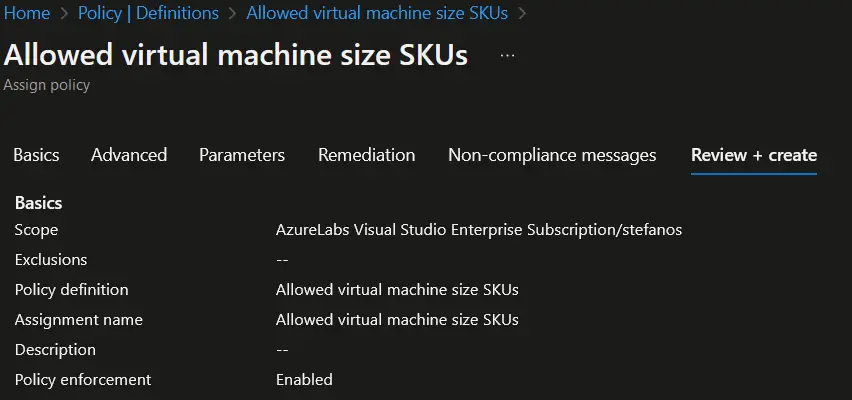
Azure Policy will now enforce the assigned policy on the selected scope (Azure subscription level, resource group level or management group level), ensuring that only the allowed Virtual Machine SKUs are used within the specified resources.
This KB article provided guidance on how to assign built-in policies in Azure policy.



