Case #
You need to enable direct RDP management of an Azure Virtual Machine over the Internet by using a public IP address. You may need this for testing purposes or in cases where you do not want to invest in other more secure alternatives, such as the Azure Bastion PaaS service or a S2S or P2S VPN with Azure VPN Gateway.
Solution #
This tutorial assumes that you have already provisioned your Azure VM with a single network interface in an Azure VNET. This network interface may or may not have an associated public IP address but it will definitely have at least one private IP address.
Follow the procedure below to enable Internet access to your Azure VM via RDP and a public IP address.
- Provision a public IP address, if you have not already done so. Create a new resource in the Azure portal by searching for "public IP address".
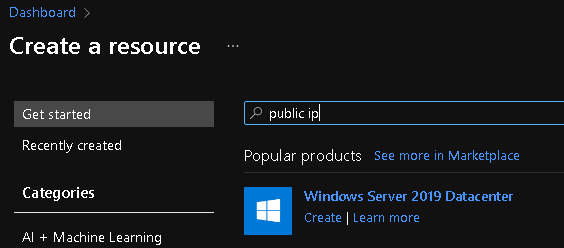
- Click on "Create".
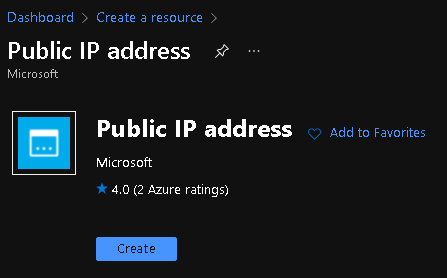
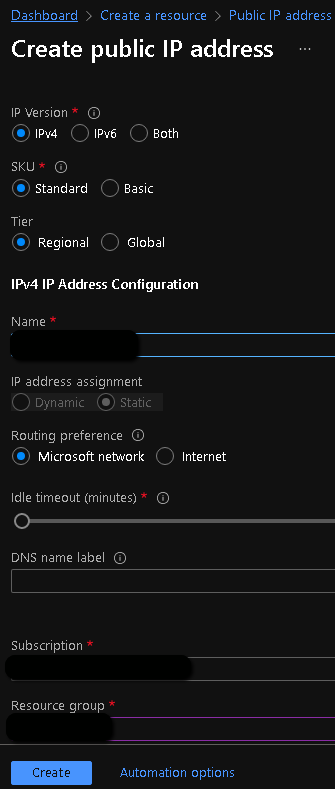
- Provide values to all mandatory configuration parameters for the public IP address resource. The routing preference parameter determines how your traffic routes between Azure and the Internet. Selecting Microsoft global network delivers traffic via Microsoft global network closest to user. Internet route option uses transit ISP network. Egress data transfer price varies based on the routing selection. Routing preference option of a Public IP can’t be changed once created. Click "Create" when done.
- Now navigate to your Azure VM resource, go to "Networking" and click on the network interface resource.
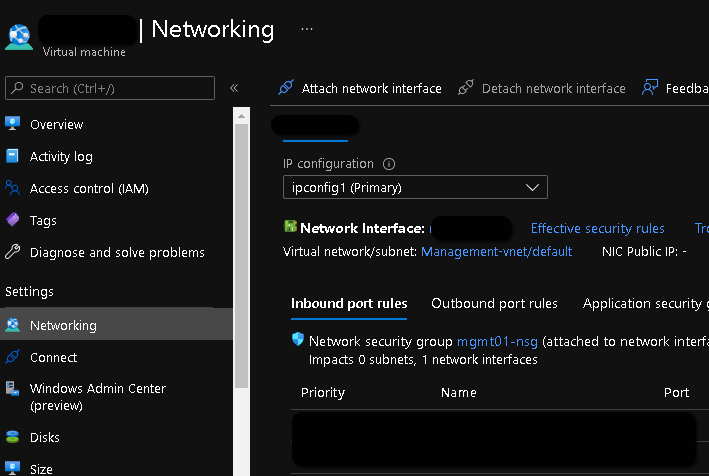
- In the network interface resource, go to "IP configurations" and click on the existing IP configuration which only has a private IP at the moment.
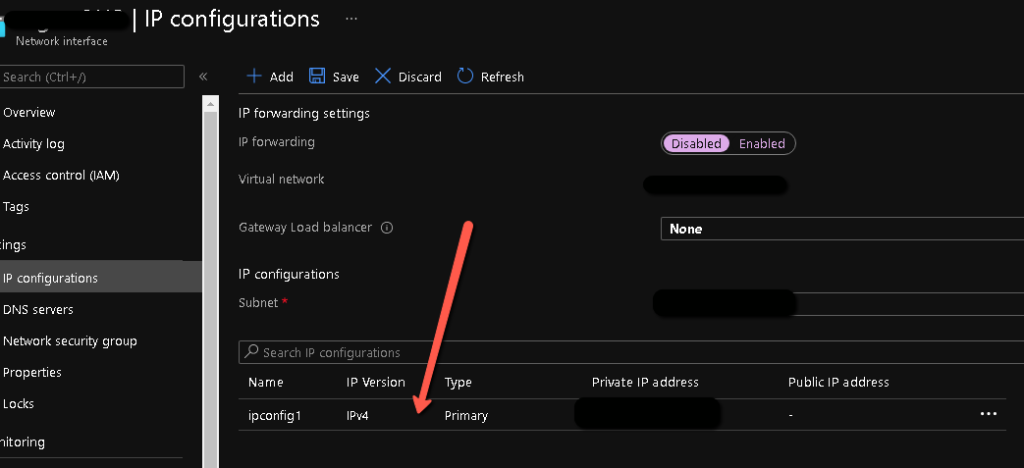
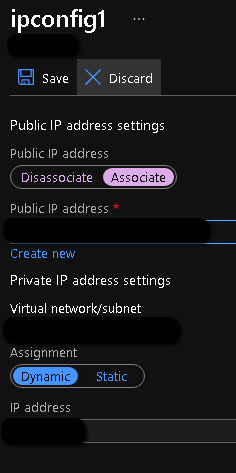
- On the next page, click on "Associate" under the Public IP address and choose the previously created public IP address, then click "Save".
- Now navigate to your VM again and edit the Network Security Group (NGS) rules of the network interface of the VM. Or you can edit this for the whole subnet where the VM belongs. In your NSG rules, allow TCP 3389 inbound to your VM from a list of public IP addresses corresponding to the Internet endpoints you will be managing the VM from.
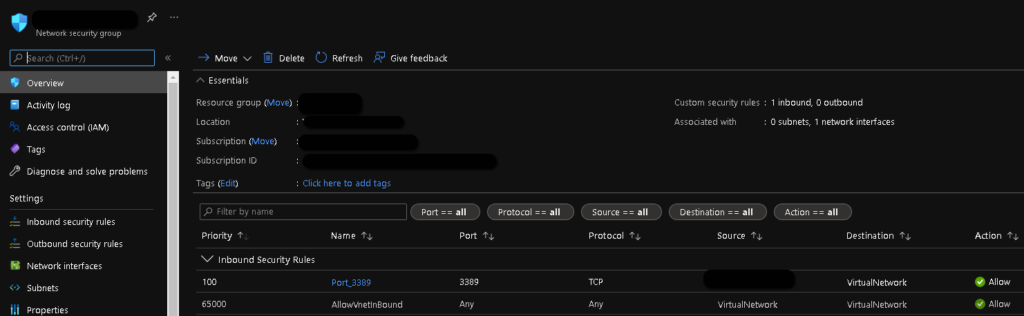
Try to make the inbound NSG rule as specific as possible in order to minimize the security attack surface.
After the above changes you should be ready to connect to the VM by RDP from the Internet. You should go the Azure VM resource, click Connect and choose the RDP tab and choose the public IP address interface, then download the corresponding connection file for your RDP client.
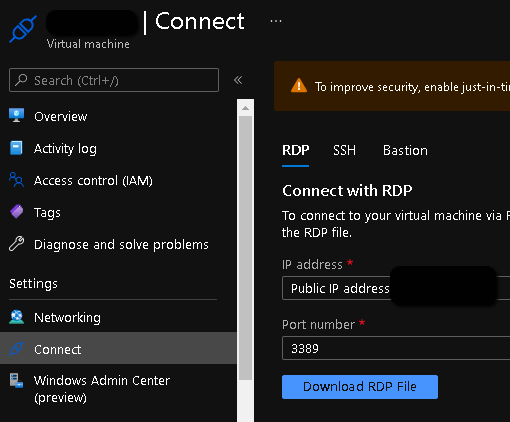
You can also enable JIT (Just In Time access) for an Azure VM. This is a feature of the Microsoft Defender for Cloud (former Azure Security Center).



