Case #
When running a .NET or other supported application in Azure App Service which utilizes web sockets and SignalR technology natively, you may encounter the following type of error message when you publish your SignalR app behind Azure Application Firewall, either embedded in Azure Application Gateway, Azure Front Door or a separately running WAF.
Error wording would include something like the following:
Failed to load resources. The server responded with a status of 404. ModSecurity Action.
Solution #
This is a known case in Web Application Firewall and is a false positive hit of the standard OWASP 3.0 security ruleset included with WAF.
This is documented as an open item in Azure and OWASP communities. As a workaround you should carry out the following steps:
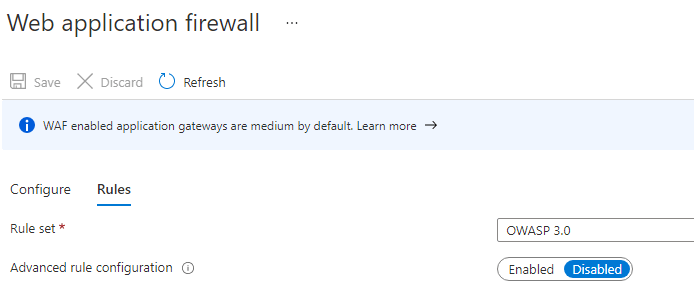
- Set your Azure Web Application Firewall to Detection Mode instead of Prevention Mode.
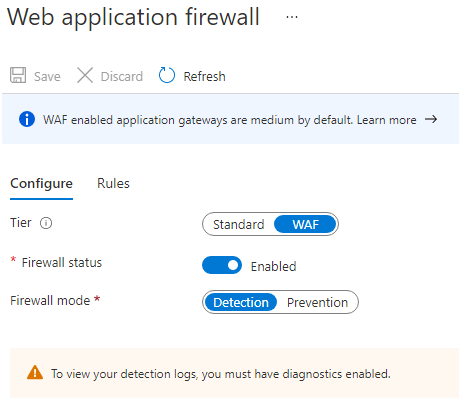
- Enable Azure WAF diagnostics in order to capture WAF logs.
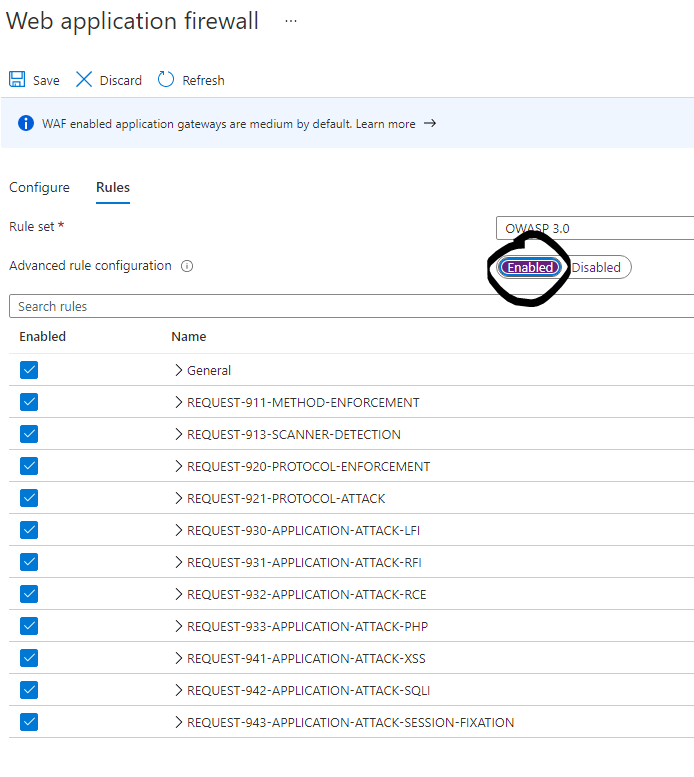
- Run your failed scenario again (this time it should be successful without errors) and then inspect your WAF logs to identify which OWASP rule(s) are hit as false positive in your scenario. Then disable these rules from the WAF configuration pane.
You should also file a bug fix request with OWASP as per https://coreruleset.org/support/ and let OWASP know that when using SignalR youget false positives against the OWASP rules, so they can make changes in future iterations of the rule set under the "Advanced Rule Configuration" section.
See more details about a similar active case at: https://github.com/SpiderLabs/owasp-modsecurity-crs/issues/1030
Sources #
https://learn.microsoft.com/en-us/archive/msdn-technet-forums/2740cc7c-40bf-4953-a7f7-048e4cdcad74
https://github.com/SpiderLabs/owasp-modsecurity-crs/issues/1030



