Case #
You have one or more on-premises computers which need to securely access Azure resources via an Azure VNET. If you dont have the necessary VPN gateway appliance to setup a site-to-site (S2S) VPN using IPSec and IKE, you can alternatively setup point-to-site (P2S) VPN.
Bear in mind that supported devices for P2S VPN are all Windows 10, Linux and Mac latest version devices as well as any other device which can support the SSTP or IKE/OpenVPN protocol.
There are various ways to configure P2S VPN connections to Azure VPN Gateway, including on-premises Active Directory domain services authentication with a Radius server, Azure AD authentication and certificate-based authentication. This article assumes the certificate-based authentication scenario.
For general guidance on troubleshooting P2S VPN issues, refer to the following KB article: https://stefanos.cloud/kb/how-to-resolve-p2s-vpn-connectivity-issues/.
Solution #
This tutorial assumes the following Azure resources are already in place:
- You have a functional Azure subscription and you are global administrator in Azure AD.
- You have created an Azure VNET which will be used for setting up the P2S VPN connectivity between your on-premises clients and the Azure VNET.
- You have setup an Azure VNET gateway resource for route-based VPN access. This should have a gateway SKU which covers your needs. You can find a handy comparison matrix of Azure VNET gateway SKUs at: https://docs.microsoft.com/en-us/azure/vpn-gateway/vpn-gateway-about-vpn-gateway-settings#gwsku.
Assuming all the above are in place, follow the procedure below to configure TLS certificate-based authentication for your new P2S VPN with Azure.
- Generate the root TLS certificate which will be uploaded to the Azure VNET gateway. The following articles provide instructions for Windows 10 and for Linux computers.
The Powershell code for root and client certificate generation (self-signed, without a CA) is the following:
Run in same elevated PS terminal:
//root
$cert = New-SelfSignedCertificate -Type Custom -KeySpec Signature -Subject "CN=P2SRootCert" -KeyExportPolicy Exportable -HashAlgorithm sha256 -KeyLength 2048 -CertStoreLocation "Cert:\CurrentUser\My" -KeyUsageProperty Sign -KeyUsage CertSign
//client
New-SelfSignedCertificate -Type Custom -DnsName P2SChildCert -KeySpec Signature -Subject "CN=P2SChildCert" -KeyExportPolicy Exportable -HashAlgorithm sha256 -KeyLength 2048 -CertStoreLocation "Cert:\CurrentUser\My" -Signer $cert -TextExtension @("2.5.29.37={text}1.3.6.1.5.5.7.3.2")- Generate client certificates and have procedure for installing the client certificates to each VPN client. You can either generate a unique certificate for each client, or you can use the same certificate for multiple clients. The advantage to generating unique client certificates is the ability to revoke a single certificate. Otherwise, if multiple clients use the same client certificate to authenticate and you revoke it, you'll need to generate and install new certificates for every client which uses that certificate. First e export the root cert from MMCconsole without the private key and Base-64 format (.cer). Then do the same export of the root cert but this time with private key (.pfx). Finally export the client certificate (.pfx) to copy it to all client computers.
- Add the VPN client address pool and configure all P2S VPN parameters in the Azure VNET gateway. First navigate in the Azure portal to your VNET gateway resource and click on the "Point-to-site configuration" pane. Click on "Configure now".
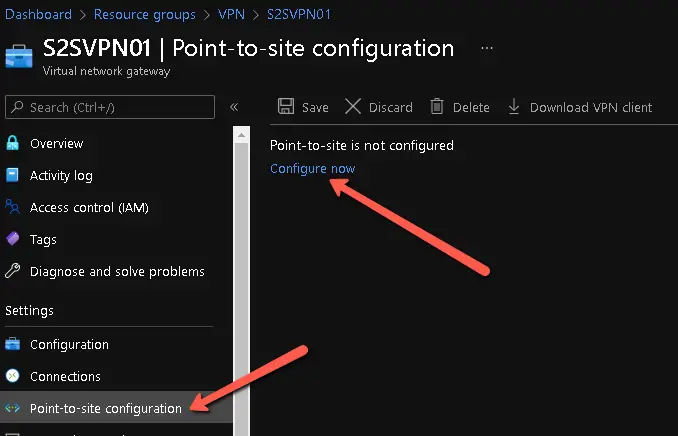
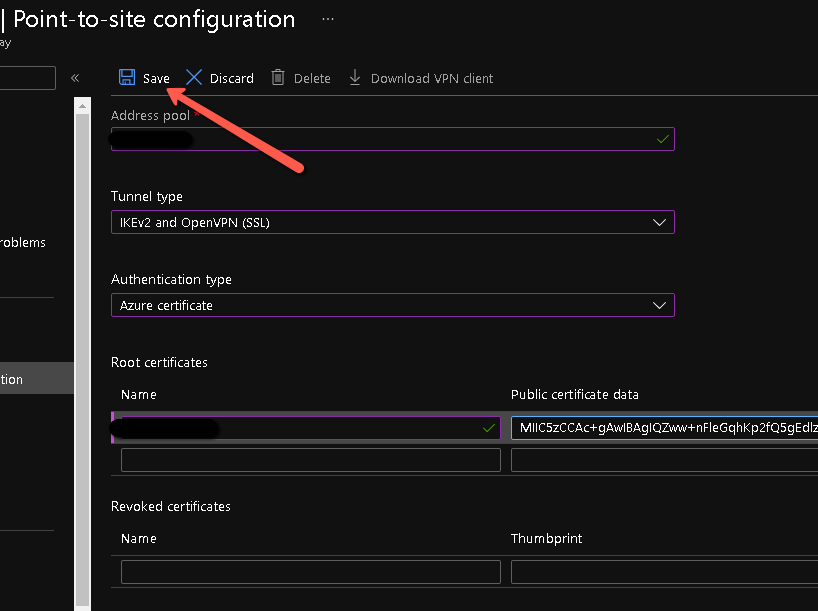
- On the next screen configure the IP address pool for your VPN clients. This should be a minimum /28 subnet and must not overlap with any subnets of the Azure VPN gateway. A /27 subnet for example would allow for 30 IP addresses to be allocated to VPN clients. Click "Save" when done. It may take some time before the P2S configuration is successfully committed.
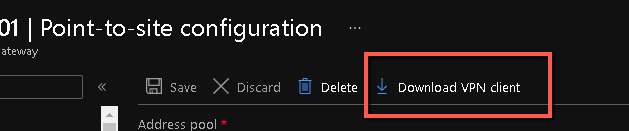
- Configure your VPN clients for Azure P2S connectivity and confirm successful connection. To connect to the virtual network gateway using P2S, each computer uses the VPN client that is natively installed as a part of the operating system. For steps to generate and install VPN client configuration files for your clients, review the following Microsoft article: https://docs.microsoft.com/en-us/azure/vpn-gateway/point-to-site-vpn-client-configuration-azure-cert. The steps at high level are the following:
- Download the VPN client configuration file and run the setup on the client computer, e.g. Windows 10 VPN client.
- Connect to the Azure P2S VPN using either the OS native client or an OpenVPN client (depending on your OS and local machine configuration).
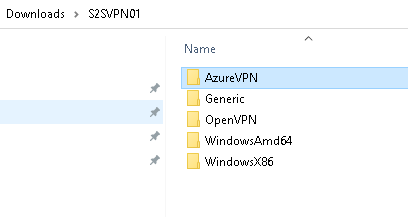
- The above will download a .zip file with the VPN client configuration files. You will need to install this alongside the VPN client .pfx certificate into all VPN clients before they can initiate a VPN connection to Azure. The VPN client configuration .zip file includes configuration packages for OpenVPN, Windows 10/11 clients and a generic .xml configuration file for third party or Linux native VPN clients.
In the case of Windows 10, after you have run the VPN configuration wizard, to initiate the VPN connection, navigate to Windows settings -->VPN settings and click on the created VPN record.
Click Connect.
- Ensure that you have received an Azure private IP address from the address pool you specified in the Azure P2S IP address pool configuration. You can do that in Windows with the ipconfig /all command and in Linux with the ifconfig command. Test an RDP connection to an existing VM which has an Azure VNET interface residing in a VNET which has peering configured with the Azure VPN gateway VNET.
Common Azure Point-to-site P2S VPN connection troubleshooting #
You may come across the following errors when trying to establish a P2S connection with Azure.
- Common error 1: "The network connection between your computer and the VPN server could not be established because the remote server is not responding. This could be because one of the network devices (e.g, firewalls, NAT, routers, etc) between your computer and the remote server is not configured to allow VPN connections. Please contact your Administrator or your service provider to determine which device may be causing the problem. (Error 809)". This is a firewall rule related issue. Check your local firewall configuration to allow ports and protocols for P2S VPN (IKEv2, SSTP, OpenVPN).
- Common error 2: "Policy match error (Error 13868)". This means the the IKE protocol parameters have a mismatch between the VPN client and VPN server. Review this article for remediation actions if you come across this error.
- For any other Azure P2S VPN connection error, review the following MS article for the top 20 possible P2S VPN issues and the respective resolution actions: https://learn.microsoft.com/en-us/azure/vpn-gateway/vpn-gateway-troubleshoot-vpn-point-to-site-connection-problems.



