Case #
Citrix is aware of a DDoS attack pattern impacting Citrix ADC and Citrix Gateway. As part of this attack, an attacker or bots can overwhelm the Citrix ADC DTLS network throughput, potentially leading to outbound bandwidth exhaustion. The effect of this attack appears to be more prominent on connections with limited bandwidth. The scope of attack is limited to a small number of customers around the world, and further, there are no known Citrix vulnerabilities associated with this event.
Solution #
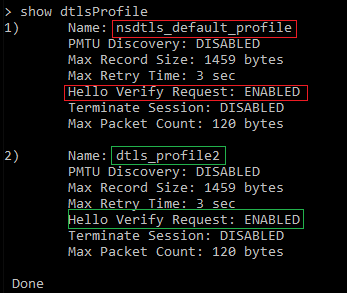
Citrix recommends administrators be cognizant of attack indicators, monitor their systems and keep their appliances up to date. To determine if a Citrix ADC or Citrix Gateway is being targeted by this attack, monitor the outbound traffic volume for any significant anomaly or spikes. Citrix has added a feature enhancement for DTLS which, when enabled, addresses the susceptibility to this attack pattern. The enhancement builds are available on the Citrix downloads page for the following versions:
Citrix ADC and Citrix Gateway 13.0-71.44 and later releases
NetScaler ADC and NetScaler Gateway 12.1-60.19 and later releases
NetScaler ADC and NetScaler Gateway 11.1-65.16 and later releasesCustomers who do not use DTLS do not need to upgrade to the enhancement build. Instead, customers are recommended to disable DTLS. Customers using DTLS are recommended to upgrade to the enhancement build and enable “HelloVerifyRequest” in each DTLS profile, as shown in the example below.