Case #
Canonical provides documentation and tools to help you get started in your journey to make Ubuntu Linux more secure. This KB article provides guidance on how to harden security in Ubuntu Linux. All security-related documentation and tools can be found under https://ubuntu.com/security.
Solution #
Ubuntu infrastructure hardening guide #
Before moving on with any security hardening tasks, you should first download and review the guide to Ubuntu infrastructure hardening: https://ubuntu.com/engage/a-guide-to-infrastructure-hardening. This includes all security design considerations for any Ubuntu on-premise, cloud or hybrid deployment.
Ubuntu Linux security features #
Ubuntu Linux is full of security features as described in a relevant security features matrix by Canonical.
https://wiki.ubuntu.com/Security/Features
| feature | 20.04 LTS | 22.04 LTS | 23.04 | 23.10 | 24.04 LTS. |
| No Open Ports | policy | policy | policy | policy | policy |
| Password hashing | sha512 | yescrypt | yescrypt | yescrypt | yescrypt |
| SYN cookies | kernel & sysctl | kernel & sysctl | kernel & sysctl | kernel & sysctl | kernel & sysctl |
| Automatic security updates | enabled | enabled | enabled | enabled | enabled |
| Kernel Livepatches | 20.04 LTS Kernel | 22.04 LTS Kernel | -- | -- | -- |
| Disable legacy TLS | policy | policy | policy | policy | policy |
| Filesystem Capabilities | kernel & userspace (default on server) | kernel & userspace (default on server) | kernel & userspace (default on server) | kernel & userspace (default on server) | kernel & userspace (default on server) |
| Configurable Firewall | ufw | ufw | ufw | ufw | ufw |
| Cloud PRNG seed | pollinate | pollinate | pollinate | pollinate | pollinate |
| PR_SET_SECCOMP | kernel | kernel | kernel | kernel | kernel |
| AppArmor | 2.13.3 | 3.0.4 | 3.0.7 | 3.0.7 | 3.0.7 |
| SELinux | universe | universe | universe | universe | universe |
| SMACK | kernel | kernel | kernel | kernel | kernel |
| Encrypted LVM | main installer | main installer | main installer | main installer | main installer |
| File Encryption | ZFS dataset encryption available, encrypted Home (eCryptfs) and ext4 encryption (fscrypt) available in universe | ZFS dataset encryption available, encrypted Home (eCryptfs) and ext4 encryption (fscrypt) available in universe | ZFS dataset encryption available, encrypted Home (eCryptfs) and ext4 encryption (fscrypt) available in universe | ZFS dataset encryption available, encrypted Home (eCryptfs) and ext4 encryption (fscrypt) available in universe | ZFS dataset encryption available, encrypted Home (eCryptfs) and ext4 encryption (fscrypt) available in universe |
| Trusted Platform Module | kernel & userspace (tpm-tools) | kernel & userspace (tpm-tools) | kernel & userspace (tpm-tools) | kernel & userspace (tpm-tools) | kernel & userspace (tpm-tools) |
| Stack Protector | gcc patch | gcc patch | gcc patch | gcc patch | gcc patch |
| Heap Protector | glibc | glibc | glibc | glibc | glibc |
| Pointer Obfuscation | glibc | glibc | glibc | glibc | glibc |
| Stack ASLR | kernel | kernel | kernel | kernel | kernel |
| Libs/mmap ASLR | kernel | kernel | kernel | kernel | kernel |
| Exec ASLR | kernel | kernel | kernel | kernel | kernel |
| brk ASLR | kernel | kernel | kernel | kernel | kernel |
| VDSO ASLR | kernel | kernel | kernel | kernel | kernel |
| Built as PIE | gcc patch (amd64, ppc64el, s390x), package list for others | gcc patch (amd64, ppc64el, s390x), package list for others | gcc patch (amd64, ppc64el, s390x), package list for others | gcc patch (amd64, ppc64el, s390x), package list for others | gcc patch (amd64, ppc64el, s390x), package list for others |
| Built with Fortify Source | gcc patch | gcc patch | gcc patch | gcc patch | gcc patch |
| Built with RELRO | gcc patch | gcc patch | gcc patch | gcc patch | gcc patch |
| Built with BIND_NOW | gcc patch (amd64, ppc64el, s390x), package list for others | gcc patch (amd64, ppc64el, s390x), package list for others | gcc patch (amd64, ppc64el, s390x), package list for others | gcc patch (amd64, ppc64el, s390x), package list for others | gcc patch (amd64, ppc64el, s390x), package list for others |
| Built with -fstack-clash-protection | gcc patch (i386, amd64, ppc64el, s390x) | gcc patch (i386, amd64, ppc64el, s390x) | gcc patch (i386, amd64, ppc64el, s390x) | gcc patch (i386, amd64, ppc64el, s390x) | gcc patch (i386, amd64, ppc64el, s390x) |
| Built with -fcf-protection | gcc patch (i386, amd64) | gcc patch (i386, amd64) | gcc patch (i386, amd64) | gcc patch (i386, amd64) | gcc patch (i386, amd64) |
| Non-Executable Memory | PAE, ia32 partial-NX-emulation | PAE, ia32 partial-NX-emulation | PAE, ia32 partial-NX-emulation | PAE, ia32 partial-NX-emulation | PAE, ia32 partial-NX-emulation |
| /proc/$pid/maps protection | kernel | kernel | kernel | kernel | kernel |
| Symlink restrictions | kernel | kernel | kernel | kernel | kernel |
| Hardlink restrictions | kernel | kernel | kernel | kernel | kernel |
| FIFO restrictions | kernel & sysctl | kernel & sysctl | kernel & sysctl | kernel & sysctl | kernel & sysctl |
| Regular file restrictions | kernel & sysctl | kernel & sysctl | kernel & sysctl | kernel & sysctl | kernel & sysctl |
| ptrace scope | kernel | kernel | kernel | kernel | kernel |
| 0-address protection | kernel | kernel | kernel | kernel | kernel |
| /dev/mem protection | kernel | kernel | kernel | kernel | kernel |
| /dev/kmem disabled | kernel | kernel | kernel | kernel | kernel |
| Block module loading | sysctl | sysctl | sysctl | sysctl | sysctl |
| Read-only data sections | kernel | kernel | kernel | kernel | kernel |
| Stack protector | kernel | kernel | kernel | kernel | kernel |
| Module RO/NX | kernel | kernel | kernel | kernel | kernel |
| Kernel Address Display Restriction | kernel | kernel | kernel | kernel | kernel |
| Kernel Address Space Layout Randomisation | kernel (i386, amd64, arm64, and s390 only) | kernel (i386, amd64, arm64, and s390 only) | kernel (i386, amd64, arm64, and s390 only) | kernel (i386, amd64, arm64, and s390 only) | kernel (i386, amd64, arm64, and s390 only) |
| Denylist Rare Protocols | kernel | kernel | kernel | kernel | kernel |
| Syscall Filtering | kernel | kernel | kernel | kernel | kernel |
| dmesg restrictions | sysctl | kernel | kernel | kernel | kernel |
| Block kexec | sysctl | sysctl | sysctl | sysctl | sysctl |
| UEFI Secure Boot (amd64) | amd64, kernel signature enforcement | amd64, kernel signature enforcement | amd64, kernel signature enforcement | amd64, kernel signature enforcement | amd64, kernel signature enforcement |
| usbguard | kernel & userspace | kernel & userspace | kernel & userspace | kernel & userspace | kernel & userspace |
| usbauth | kernel & userspace | kernel & userspace | kernel & userspace | kernel & userspace | kernel & userspace |
| bolt | kernel & userspace | kernel & userspace | kernel & userspace | kernel & userspace | kernel & userspace |
| thunderbolt-tools | kernel & userspace | kernel & userspace | kernel & userspace | kernel & userspace | kernel & userspace |
| Kernel Lockdown | integrity only, no confidentiality | integrity only, no confidentiality | integrity only, no confidentiality | integrity only, no confidentiality | integrity only, no confidentiality |
Ubuntu Pro #
By making use of a free Ubuntu Pro subscription you can ensure that you maximize potential for security features in your Ubuntu installation. Subscribe for free with an Ubuntu Pro account and link up to 5 machines to this subscription. Pricing is free for personal usage.
Visit https://ubuntu.com/pro/dashboard after logging into your Ubuntu Pro account. An example of a free Ubuntu Pro account dashboard is shown below.
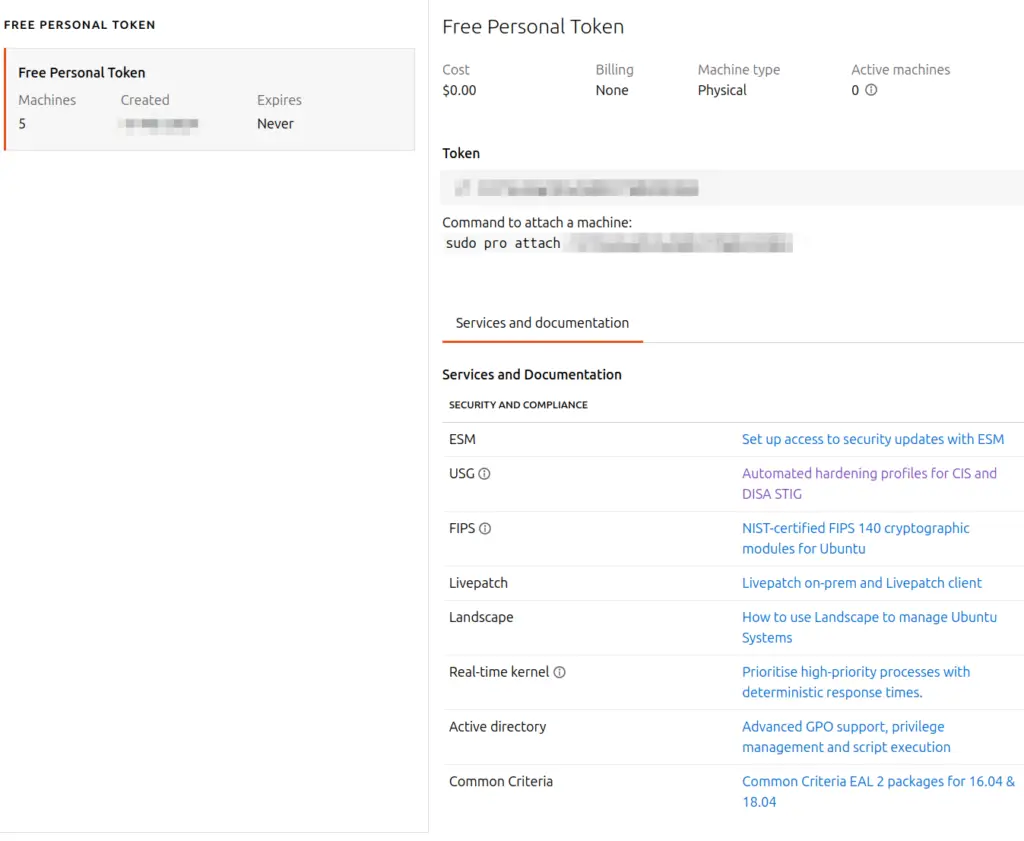
Enable any additional features in Ubuntu Pro, as shown in the screenshot below.
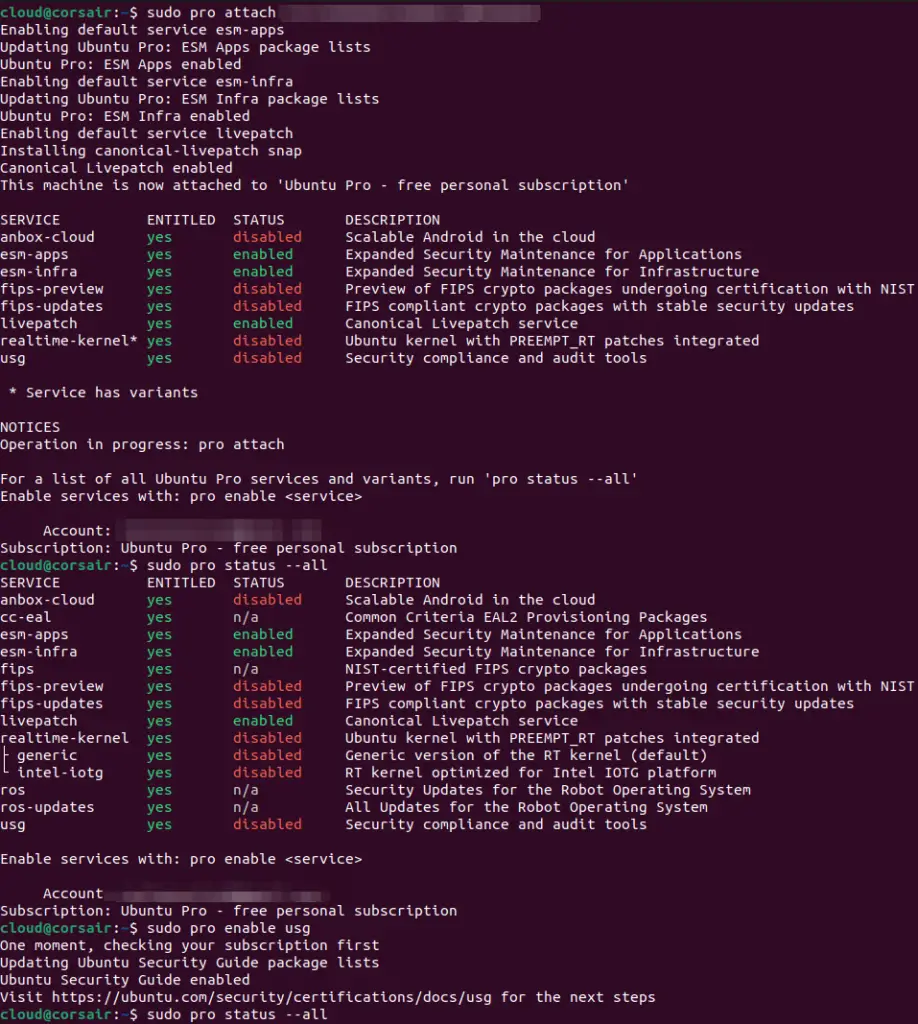
With Ubuntu Pro enabled, carry out the following action items for Ubuntu Linux machine security hardening.
Ubuntu security certifications and hardening #
Canonical Ubuntu provides the following security certifications and compliance controls.
- Utilize FIPS configuration if needed.
- Make the most of CIS security controls.
- Tthe Security Technical Implementation Guides (STIG) are developed by the Defense Information System Agency (DISA) for the U.S. Department of Defense (DoD).
Ubuntu Livepatch #
Livepatch eliminates the need for unplanned maintenance windows for high and critical severity kernel vulnerabilities by patching the Linux kernel while the system runs. You can downtime and keep uninterrupted service with the Ubuntu Livepatch service for up to 10 years.
Expanded Security Maintenance (ESM) #
ESM enables continuous vulnerability management for critical, high and medium CVEs. You can review the terms and 5-year vs 10-year coverage for Ubuntu on the following page: https://ubuntu.com/security/esm.
CVE reports #
The Common Vulnerabilities and Exposures (CVE) system is used to identify, define, and catalog publicly disclosed cybersecurity vulnerabilities. Canonical keeps track of all CVEs affecting Ubuntu, and releases a security notice when an issue is fixed. Canonical also produces Open Vulnerability and Assessment Language (OVAL) data, which is machine-readable, to enable auditing for CVEs and to determine whether a particular patch, via an Ubuntu Security Notice (USN), is appropriate for the local system. Also refer to the Ubuntu Security Notices for more details.
Ubuntu OCI images #
Canonical provides hardened OCI container images, with stable tracks from development to production. Canonical provides up to ten years guaranteed security maintenance from Canonical’s trusted repositories. You can browse the full repository of images on the relevant Docker Hub registry page at: https://hub.docker.com/u/ubuntu.
Canonical cybersecurity webinar #
Last but not least, it is highly recommended to watch the cybersecurity webinar by Canonical, in which the following topics are discussed:
- Provide an introduction to cybersecurity and zero trust.
- Highlight the common challenges faced in the implementation of cybersecurity programs, including challenges in vulnerability management, secure configuration of software and defenses against malware.
- Discuss how Canonical and Ubuntu can help manage these challenges and lay the foundation of a successful cybersecurity program.



