Case #
You need to change the security identifier SID in Windows operating systems. This KB article provides guidance on how to change the security identifier SID in Windows operating systems. There are many entities in the Windows operating system which have an associated SID, some of which are the following:
- Local users and groups
- Domain users and groups
- Computer objects
- Active Directory domains and forests
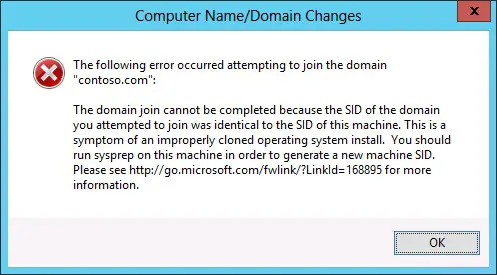
More specifically, changing the SID of a Windows computer may be required if you have used a misconfigured Windows OS image, which, if used to deploy new machines, may lead to a duplicate SID issue. The duplicate SID issue usually manifests with the following error when trying to join a machine to an Active Directory domain.
The following error occurred attempting to join the domain [domain name]. The domain join cannot be completed because the SID of the domain you attempted to join was identical to the SID of this machine. This is a symptom of an improperly cloned operating system install. You should run sysprep on this machine in order to generate a new machine SID.
Every security account, such as a user, group, or computer, has a unique SID. Access permissions are granted or denied to SIDs for resources, such as files, folders, printers, Microsoft Exchange mailboxes, Microsoft SQL Server databases, objects that are stored in Active Directory, and any data that is protected by the Windows Server security model. A SID contains header information and a set of relative identifiers that identify the domain and the security account. In a domain, each domain controller can create accounts and issue a unique SID to every account. It must be noted that there are both machine SIDs and domain SIDs (https://learn.microsoft.com/en-us/archive/blogs/aaron_margosis/machine-sids-and-domain-s).
This article provides guidance on how to change the security identifier SID in Windows operating systems, to resolve the duplicate SID issue.
Solution #
Before moving forward with any action, it is highly recommended to read a relevant article on Windows Security Identifiers (SID) to get a better grasp of how they work.
AD Domain SID #
Run the following command to get the current AD domain SID. There is no supported way to change the AD domain SID.
Import-Module ActiveDirectory
#Get the SID of all domains in an AD forest
(Get-ADForest).Domains| %{Get-ADDomain -Server $_} | Select-Object name, domainsid
#Get the SID of a specific AD domain
Get-AdDomain | Select-Object name, domainsidUser or group SID #
Run the following command to get the current local user SID.
Get-LocalUser -Name "[username]" | Select-Object sidRun the following command to get the current domain user SID.
Import-Module ActiveDirectory
Get-AdUser -Identity [username-SaMAccount] | Select Name, SID, UserPrincipalNameRun the following command to get the current local group SID.
Get-LocalGroup "[groupname]" | select SIDRun the following command to get the current domain group SID.
Import-Module ActiveDirectory
Get-ADGroup -Identity "[groupname]" | Select-Object Name, SIDComputer SID #
To get the SID of a workgroup computer, you need to download and run the PsGetSID command line tool, which is part of the SysInternals suite.
To get the SID of a domain-joined machine, run the following Powershell cmdlet.
Get-ADComputer -Filter * | Select-Object Name, SID
Get-ADComputer "[computername]" | Select-Object Name, SIDTo change the computer SID of a Windows computer you can try the following methods.
- As the error message itself suggests, the most direct method of changing the machine SID is by running sysprep on it. Sysprep is a Windows utility which generalizes an OS image. Generalizing an image removes computer-specific information such as installed drivers and the computer security identifier (SID). You can either use Sysprep by itself or Sysprep with an unattend answer file to generalize your image and make it ready for deployment. Details about running sysprep can be found at https://learn.microsoft.com/en-us/windows-hardware/manufacture/desktop/sysprep--generalize--a-windows-installation?view=windows-11. To run sysprep manually, run the following tasks:
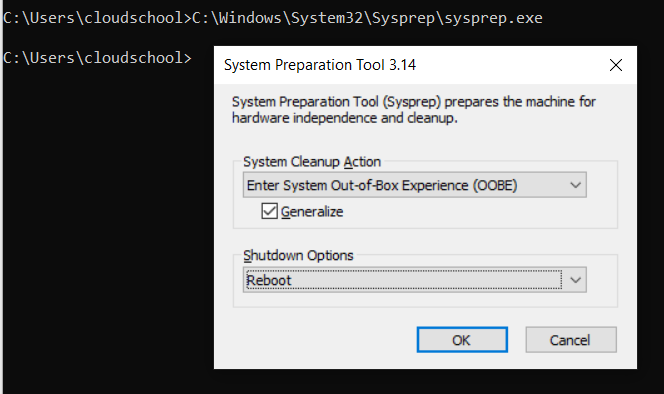
- Open an elevated command prompt and run the following command:
C:\Windows\System32\Sysprep\sysprep.exeIn the pop-up form, select system cleanup action "Enter System OOBE", check the "Generalize" checkbox and select "reboot" or "shutdown" as the shutdown option and click OK.
- Since running sysprep is a quite intrusive action, which will most likely affect already installed applications and drivers, it is not recommended in machines already in production. An alternative for systems already in an Active Directory production environment is to first check for and cleanup any duplicate SID by running the ntdsutil utility. Details about ntdsutil can be found at: https://learn.microsoft.com/en-us/troubleshoot/windows-server/identity/ntdsutil-find-clean-duplicate-security-identifiers. Carry out the following steps to detect and cleanup duplicate SID from the SAM database.
- In an elevated command prompt, run ntdsutil.
- At the Ntdsutil command prompt, type security account management, and then press Enter.
- To connect to the server that stores your Security Account Maintenance (SAM) database, type
connect to serverDNSNameOfServerat the SAM command prompt, and then press Enter. - At the SAM command prompt, type check duplicate sid (or cleanup duplicate sid for cleaning up duplicate SID), and then press Enter.
- Microsoft used to provide the NewSID utility as part of the SysInternals suite but it was later determined that this tool would not provide a sufficient solution, hence it is no longer available for download. Microsoft does not support images that are prepared using NewSID, they only support images that are prepared using SysPrep. Microsoft has not tested NewSID for all deployment cloning options. You can still use the PsGetSID as part of the SysInternals suite, to identity SID property and map it to object names, for both workgroup and AD accounts.
- One viable option for changing a Windows computer SID in production environments is the SIDCHG command line tool, which comes in both 32-bit and 64-bit versions. This is a paid tool, which is licensed based on your usage scenario. SIDCHG (SIDCHG64 on 64-bit Windows) 3.0i is a command-line utility to modify local computer SID and computer name, for Windows 2022/11/2019/2016/10/8.1/2012 R2/8/2012/7/2008 R2. It replaces current computer SID with new random SID. In addition, it changes the WSUS ID for Windows Updates, the MachineGuid, the Machine ID, the Device Identifier for modern Windows apps, the MSDTC CID, the Dhcpv6 DUID, the SQL Server Master database, the encryption state to preserve encrypted files, Windows Action Center settings, Certificates and other encrypted stored information. Preservation of credentials stored in Windows Vault is possible with prior preparation of Vault backup. Optionally OneDrive can be reset. A reboot is needed after the SID change.
Run the following procedure to have the computer SID changed with the SIDCHG command line tool.
- Firstly, activate the SIDCHG software.
- Then run the command with any required parameters as per your scenario. Consult the software vendor's documentation for each command parameter usage. In the example below the only parameter provided is the /R parameter for automatic system reboot after the SID change. Click Yes to continue.
- Click OK to continue and wait until the system is explicitly restarted or shutdown.
- After system reboot, login to the computer again to verify that the computer SID has been changed, by running the PsGetSID tool from SysInternals.
Bear in mind that before you change the machine SID you need to carry out the following actions:
- Take a full backup of the machine whose SID will be changed, whether that be a bear metal backup or operating system disk backup of a physical machine or a full backup of a virtual machine or container. A VM snapshot may also be handy but a full backup is always recommended. If you compare a snapshot with a backup, for example a Windows System State backup, the snapshots are dependent of the virtual machine, while the System State backup is not, it is independent.
- Audit the machine(s) in question to understand if operating system or application related functionality and features are dependent on the machine SID to operate. This can include application and SQL connection strings and application license files which may have dependencies on the machine SID. If this is the case, create a plan to make necessary changes to accommodate the change.
- Ensure that any real-time antivirus and antimalware software is turned off / disabled before you run the SID change application.
- Ensure that no users will be able to power off, shutdown or logon to the system whose SID is being changed, during the SID change procedure.
This article provided guidance on how to change the security identifier SID in Windows operating systems.
Sources #
- https://learn.microsoft.com/en-us/archive/blogs/deploymentguys/sysprep-machine-sids-and-other-myths
- https://learn.microsoft.com/en-us/archive/blogs/markrussinovich/the-machine-sid-duplication-myth-and-why-sysprep-matters
- https://learn.microsoft.com/en-us/archive/blogs/aaron_margosis/machine-sids-and-domain-sids
- https://learn.microsoft.com/en-us/windows-server/identity/ad-ds/manage/understand-security-identifiers



